2016/10 New 70-465: Designing Database Solutions for Microsoft SQL Server 2014 Exam Questions Updated Today!
Free Imstant Download 70-465 Exam Dumps (PDF & VCE) 160Q&As from Braindump2go.com Today!
100% Real Exam Questions! 100% Exam Pass Guaranteed!
1.|2016/10 Latest 70-465 Exam Dumps (PDF & VCE) 160Q&As Download:
http://www.braindump2go.com/70-465.html
2.|2016/10 Latest 70-465 Exam Questions & Answers:
https://drive.google.com/folderview?id=0B9YP8B9sF_gNVGJOa0pteHZWMXM&usp=sharing
QUESTION 17
Drag and Drop Question
You plan to deploy SQL Server 2014.
Your company identifies the following monitoring requirements:
– Tempdb must be monitored for insufficient free space.
– Deadlocks must be analyzed by using Deadlock graphs.
You need to identify which feature meets each monitoring requirement.
Which features should you identify? To answer, drag the appropriate feature to the correct monitoring requirement in the answer area.
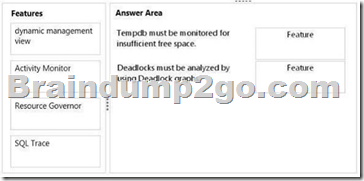
Answer:
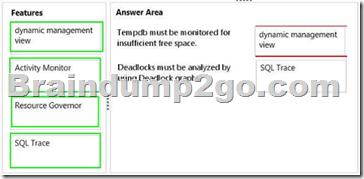
Explanation:
– You can use the sys.dm_db_file_space_usage dynamic management view to monitor the disk space used by the user objects, internal objects, and version stores in the tempdb files. Additionally, to monitor the page allocation or deallocation activity in tempdb at the session or task level, you can use the sys.dm_db_session_space_usage and sys.dm_db_task_space_usage dynamic management views.
These views can be used to identify large queries, temporary tables, or table variables that are using a large amount of tempdb disk space.
– Use SQL Server Profiler to identify the cause of a deadlock. A deadlock occurs when there is a cyclic dependency between two or more threads, or processes, for some set of resources within SQL Server. Using SQL Server Profiler, you can create a trace that records, replays, and displays deadlock events for analysis.
– SQL Server Profiler and SQL Server Management Studio use a deadlock wait-for graph to describe a deadlock. The deadlock wait-for graph contains process nodes, resource nodes, and edges representing the relationships between the processes and the resources.
Reference: Troubleshooting Insufficient Disk Space in tempdb Reference: Analyze Deadlocks with SQL Server Profiler
QUESTION 18
You plan to create a database.
The database will be used by a Microsoft .NET application for a special event that will last for two days.
During the event, data must be highly available.
After the event, the database will be deleted.
You need to recommend a solution to implement the database while minimizing costs.
The solution must not affect any existing applications.
What should you recommend? More than one answer choice may achieve the goal. Select the BEST answer.
A. SQL Server 2014 Enterprise
B. SQL Server 2014 Standard
C. SQL Azure
D. SQL Server 2014 Express with Advanced Services
Answer: B
Explanation:
Programmability (AMO, ADOMD.Net, OLEDB, XML/A, ASSL) supported by Standard and Enterpirse editions only.
Reference: Features Supported by the Editions of SQL Server 2014
QUESTION 19
You are designing a database named DB1.
Changes will be deployed to DB1 every Wednesday night.
You need to recommend a strategy to deploy the changes to DB1.
The strategy must meet the following requirements:
– The strategy must not disrupt backup operations.
– DB1 must be unavailable to users while the changes are deployed.
– You must be able to undo quickly the entire operation.
What should you recommend? More than one answer choice may achieve the goal. Select the BEST answer.
A. Perform a copy-only database backup before the changes are deployed.
If the deployment fails, restore the database to another server and recover the original
Objects from the restored database.
B. Create a database snapshot.
If the deployment fails, recover the objects from the database snapshot.
C. Create a database snapshot.
If the deployment fails, revert the database to the database snapshot.
D. Perform a full database backup before the changes are deployed.
If the deployment fails, restore the database to another server and recover the original
objects from the restored database.
Answer: C
QUESTION 20
Drag and Drop Question
You plan to deploy SQL Server 2014.
You are designing two stored procedures named SP1 and SP2 that have the following requirements:
– Prevent data read by SP1 from being modified by other active processes.
– Prevent SP2 from performing dirty reads.
You need to recommend the isolation level for each stored procedure.
The solution must maximize concurrency.
Which isolation levels should you recommend? To answer, drag the appropriate isolation level to the correct stored procedure in the answer area.
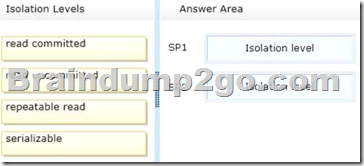
Answer:
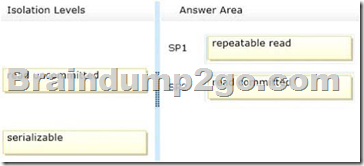
Explanation:
– REPEATABLE READ
This isolation level includes the guarantees given by SNAPSHOT isolation level.
In addition, REPEATABLE READ guarantees that for any row that is read by the transaction, at the time the transaction commits the row has not been changed by any other transaction.
Every read operation in the transaction is repeatable up to the end of the transaction.
– Committed Read is SQL Server’s default isolation level. It ensures that an operation will never read data another application has changed but not yet committed.
QUESTION 21
Drag and Drop Question
You are designing an authentication strategy for a new server that has SQL Server 2014 installed.
The strategy must meet the following business requirements:
– The account used to generate reports must be allowed to make a connection during certain hours only.
– Failed authentication requests must be logged.
You need to recommend a technology that meets each business requirement.
The solution must minimize the amount of events that are logged.
Which technologies should you recommend? To answer, drag the appropriate solution to the correct business requirement in the answer area.
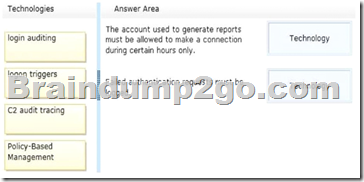
Answer:
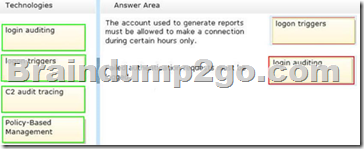
Explanation:
– Logon triggers fire stored procedures in response to a LOGON event.
This event is raised when a user session is established with an instance of SQL Server.
Logon triggers fire after the authentication phase of logging in finishes, but before the user session is actually established.
You can use logon triggers to audit and control server sessions, such as by tracking login activity, restricting logins to SQL Server, or limiting the number of sessions for a specific login.
– Login auditing can be configured to write to the error log on the following events.
– Failed logins
– Successful logins
– Both failed and successful logins
Incorrect:
– C2 audit mode can be configured through SQL Server Management Studio or with the c2 audit mode option in sp_configure. Selecting this option will configure the server to record both failed and successful attempts to access statements and objects.
QUESTION 22
You are designing a SQL Server database for an order fulfillment system.
You create a table named Sales.Orders by using the following script:
Each order is tracked by using one of the following statuses:
– Fulfilled
– Shipped
– Ordered
– Received
You need to design the database to ensure that you can retrieve the status of an order on a given date.
The solution must ensure that new statuses can be added in the future.
What should you do? More than one answer choice may achieve the goal. Select the BEST answer.
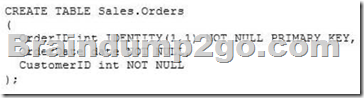
A. To the Sales.Orders table, add a column named Status that will store the order status.
Update the Status column as the order status changes.
B. Create a new table named Sales.OrderStatus that contains three columns named OrderID,
StatusDate, and Status. Insert new rows into the table as the order status changes.
C. Implement change data capture on the Sales.Orders table.
D. To the Sales.Orders table, add three columns named FulfilledDate, ShippedDate, and
ReceivedDate. Update the value of each column from null to the appropriate date as the
order status changes.
Answer: A
QUESTION 23
You have two SQL Server 2012 instances named SQLDev and SQLProd.
You plan to create a new database on SQLProd that will use SQL Server Authentication.
You need to ensure that when the new database is copied from SQLProd to SQLDev, users can connect to the database on SQLDev if they do not have a login on the SQLDev instance.
What should you use? More than one answer choice may achieve the goal. Select the BEST answer.
A. SQL Server Integration Services (SSIS) scripts
B. Extended Events
C. Triggers
D. SQL Server Analysis Services (SSAS) scripts
E. Contained database
Answer: E
Explanation:
A fully contained database includes all the settings and metadata required to define the database and has no configuration dependencies on the instance of the SQL Server Database Engine where the database is installed.
!!!RECOMMEND!!!
1.Braindump2go|2016/10 Latest 70-465 Exam Dumps (PDF & VCE) 160Q&As Download:
http://www.braindump2go.com/70-465.html
2.Braindump2go|2016/10 Latest 70-465 Exam Questions & Answers:
https://drive.google.com/folderview?id=0B9YP8B9sF_gNVGJOa0pteHZWMXM&usp=sharing