2016/09 New Microsoft 70-243: Administering and Deploying System Center 2012 Configuration Manager Exam Questions Released Today!
Free Instant Download 70-243 Exam Dumps (PDF & VCE) 167Q&As from Braindump2go.com Today!
100% Real Exam Questions! 100% Exam Pass Guaranteed!
1.|2016/09 Latest 70-243 Exam Dumps (PDF & VCE) 167Q&As Download:
http://www.braindump2go.com/70-243.html
2.|2016/09 Latest 70-243 Exam Questions & Answers:
https://drive.google.com/folderview?id=0B75b5xYLjSSNfkdreTRTTVpZRTBaMmMtbUFuU0RnNzBWNDYyOXNlUndGUEhzOTVabkFzdEk&usp=sharing
QUESTION 18
Your network contains a System Center 2012 Configuration Manager environment.
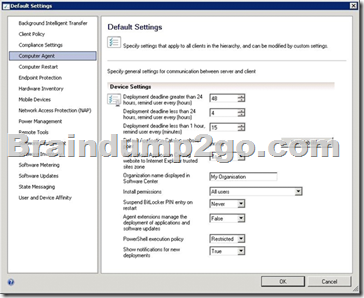
You need to change the organization name displayed by Configuration Manager.
Which settings should you modify from the Configuration Manager console?
A. Client Policy
B. Computer Agent
C. User and Device Affinity
D. Compliance Settings
Answer: B
Explanation:
Administration -> Client Settings -> Default Client Settings -> Computer Agent
QUESTION 19
Your network contains a System Center 2012 Configuration Manager environment. Software Inventory and Hardware Inventory are enabled for all of the client computers. All of the client computers have an Application named App1 installed. App1 saves files to the C:\ABC folder.
All of the files saved by App1 have a file name extension of .abc.
You configure Software Inventory to inventory all of the files that have the .abc extension and the .exe extension. After six months, you discover that some of the client computers fad to inventory .abc fees. Al of the client computers inventory .exe files.
You need to ensure that the .abc files are inventoried.
What should you do?
A. Modify C:\Program Files\App1\NO_SMS_On_Drive.sms.
B. Delete C:\Program Files\App1\NO-SMS_On_Drive.sms.
C. Modify C:\ABC\Skpswi.dat.
D. Delete C:\ABC\Skpswi.dat.
Answer: D
Explanation:
http://technet.microsoft.com/en-us/library/hh691018.aspx
How to Exclude Folders from Software Inventory in Configuration Manager
You can create a hidden file named Skpswi.dat and place it in the root of a client hard drive to exclude it from System Center 2012 Configuration Manager software inventory. You can also place this file in the root of any folder structure you want to exclude from software inventory. This procedure can be used to disable software inventory on a single workstation or server client, such as a large file server.
Note: Software inventory will not inventory the client drive again unless this file is deleted from the drive on the client computer.
QUESTION 20
Your network contains a System Center 2012 Configuration Manager environment.
In Default Client Agent Settings, you enable Hardware Inventory and Software Inventory.
You discover that a group of client computers fails to report software inventory data.
The client computers report hardware inventory data.
You confirm that Configuration Manager can deploy Applications to the group of client computers. You need to identify what is causing the reporting issue.
Which log files should you review? (Choose all that Apply.)
A. Filesystemfile.log
B. Dataldr.log
C. Mp_sinv.log
D. Inventoryagent.log
E. Hman.log
Answer: AD
Explanation:
http://technet.microsoft.com/en-us/library/hh427342.aspx
FileSystemFile.log
log for software inventory and file collection
InventoryAgent.log
logs DDRs (Discovery Data Records) for hardware and software
More information:
dataldr.log
Records information about the processing of Management Information Format (MIF) files and hardware inventory in the Configuration Manager database.
The question states “You discover that a group of client computers fails to report software inventory data”. As per the above definition, dataldr.log is used for the processing of MIF files and Hardware Inventory.
QUESTION 21
Note: This question is part of a series of questions that use the same set of answer choices. n answer choice may be correct for more than one question in the series.
Your network contains a System Center 2012 Configuration Manager environment.
The network contains 10 database servers that run Microsoft SQL Server 2008.
You have a configuration baseline that is used to monitor the database servers.
You add new configuration items to the configuration baseline.
Two days later, you discover that only eight of the database servers report any information about the new configuration items.
You need to identify whether the new configuration items downloaded to the database servers. Which log file should you review?
A. Hman.log
B. Sitestat.log
C. Dcmagent.log
D. Wsyncmgr.log
E. Ccm.log
F. Contenttransfermanager.log
G. Sdmagent.log
H. Rcmctri.log
I. Ciagent.log
J. Smsexec.log
K. Locationservices.log
Answer: I
Explanation:
Ciagent.log
Not related to US foreign security policy but provides information about processing
configuration items, including software updates.
Incorrect:
Not B: Sitestat.log: Records the monitoring process of all site systems.
QUESTION 22
Note: This question is part of a series of questions that use the same set of answer choices.
An answer choice may be correct for more than one question in the series.
You create a deployment to install Microsoft Office 2010.
The deployment targets 5,000 client computers on the network.
Two weeks after you create the deployment, you discover that Office 2010 fails to install on a client computer named Computer 1.
You need to identify whether Computer1 started downloading the Application of Office 2010. Which log file should you review?
A. Locationservices.log
B. Ccm.log
C. Sdmagent.log
D. Sitestat.log
E. Rcmctrl.log
F. Dcmagent.log
G. Contenttransfermanager.log
H. Smsexec.log
I. Wsyncmgr.log
J. Ciagent.log
K. Hman.tog
Answer: G
Explanation:
How to find if download start, TS using log file: ContentTransferManager.log SDMAgent.log – desired configuration management and contains the tracking process of remediation and compliance. dcmagent.log – Provides high-level information about the evaluation of assigned configuration baselines CIAgent.log – Tracks the process of remediation and compliance Updateshandler.log – provides more informative details on installing the software updates wsyncmgr.log -Provides information about the software updates synchronization process
Smsexec.log – Records processing of all site server component threads. ContentTransferManager.log
– Schedules the Background Intelligent Transfer Service (BITS) or the Server
QUESTION 23
Note: This question is part of a series of questions that use the same set of answer choices.
An answer choice may be correct for more than one question in the series.
Your network contains a System Center 2012 Configuration Management environment.
The environment contains a Central Administration site and two primary child sites named Child1 and Child2.
You create a new Application on the Central Administration site.
You view the new Application on Child 1, but the new Application fails to appear on Child2.
You need to identify whether the Application transferred to Child2.
Which log file should you review?
A. Locabonservices.log
B. Smsexec.log
C. Ccm.log
D. Sdmagent.log
E. Dcmagent.log
F. Rcmctrl.log
G. Wsyncmgr.log
H. Ciagent.log
I. Hman.log
J. Contenttransfermanager.log
K. Sitestat.log
Answer: F
Explanation:
Rcmctrl.log
Replication related information.
Incorrect:
Not A: Locatonservices.log Finds management points and distribution points.
Not B: Smsexec.log Records processing of all site server component threads.
Not C: Ccm.log
Client Configuration Manager tasks.
Not D: Sdmagent.log
Shared with the Configuration Manager feature desired configuration management and
contains the tracking process of remediation and compliance.
Not E: Dcmagent.log
Provides high-level information about the evaluation of assigned configuration baselines
and desired configuration management processes.
Not G: Wsyncmgr.log
Provides information about the software updates synchronization process.
Not H: Ciagent.log
Not related to US foreign security policy but provides information about processing
configuration items, including software updates.
Not I: Hman.log
Records site configuration changes, and publishes site information in Active Directory
Domain Services.
Not J: ContentTransferManager.log
Schedules the Background Intelligent Transfer Service (BITS) or the Server Message Block
(SMB) to download or to access SMS packages.
Not K: Sitestat.log
Records the monitoring process of all site systems.
!!!RECOMMEND!!!
1.|2016/09 Latest 70-243 Exam Dumps (PDF & VCE) 167Q&As Download:
http://www.braindump2go.com/70-243.html
2.|2016/09 Latest 70-243 Exam Questions & Answers:
https://drive.google.com/folderview?id=0B75b5xYLjSSNfkdreTRTTVpZRTBaMmMtbUFuU0RnNzBWNDYyOXNlUndGUEhzOTVabkFzdEk&usp=sharing