MICROSOFT NEWS: 70-663 Exam Questions has been Updated Today! Get Latest 70-663 VCE and 70-663 PDF Instantly! Welcome to Download the Newest Braindump2go 70-663 VCE&70-663 PDF Dumps: http://www.braindump2go.com/70-663.html (291 Q&As)
Laest 70-663 PDF Dumps and 70-663 VCE Dumps can be downloaded from Braindump2go Now! This New Updated 70-663 Exam Dumps has 291q in all! All Braindump2go 70-663 Exam Questions and Answers are formulated and verified by experienced IT professionals! We guarantee all of you can pass 70-663 Exam successfully!
Exam Code: 70-663
Exam Name: Pro: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010
Certification Provider: Microsoft
Corresponding Certifications: MCITP, MCITP: Enterprise Messaging Administrator on Exchange 2010
70-663 Dumps,70-663 Dumps PDF,70-663 Dumps VCE,70-663 PDF,70-663 VCE,70-663 Study Guide,70-663 Braindump,70-663 Book,70-663 Exam Questions,70-663 Practice Test,70-663 Practice Exam,70-663 eBook,70-663 Preparation
QUESTION 31
You have an Exchange Server 2010 organization.
All users on the network connect to their mailboxes by using Microsoft Office Outlook.
Your company’s compliance policy states that:
– A copy of e-mail messages sent to the human resources department from the Internet must be archived
– All archived e-mail messages must be stored on a third-party archival server
You need to recommend a solution that meets the requirements of the compliance policy.
What should you include in the solution?
A. Journal rules
B. Personal archives
C. Retention Policies
D. Transport Protection Rules
Answer: A
Explanation:
Questions states that a copy must be archived. Personal archives actually moves the message. So the Journaling is a solution as you can specify journaling email that is located outside Exchange environment.
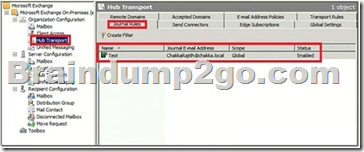
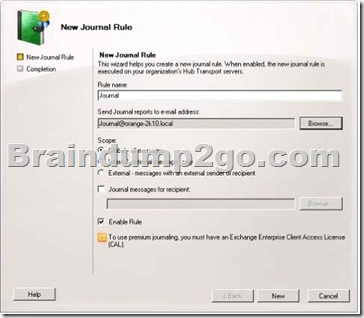
You can implement targeted journaling rules by specifying the SMTP address of the recipient you want to journal. The recipient can be an Exchange mailbox, distribution group, or a contact. These recipients may be subject to regulatory requirements, or they may be involved in legal proceedings where e-mail messages or other communications are collected as evidence.
All messages sent to or from the journaling recipients you specify in a journaling rule are journaled. The journaling mailbox is used for collecting journal reports.
A journal report is the message that the Journaling agent generates when a message matches a journal rule.
The original message that matches the journal rule is included unaltered [nepakeistas] as an attachment to the journal report. The body of a journal report contains information from the original message such as the sender e-mail address, message subject, message-ID, and recipient e-mail addresses.
http://technet.microsoft.com/en-us/library/aa998649.aspx
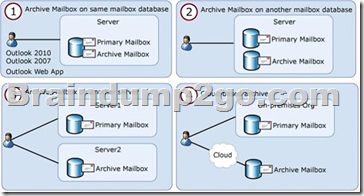
Personal archives (also known as on-premises archives) help you regain control of your organization’s messaging data by eliminating the need for personal store (.pst) files and allowing users to store messages in an archive mailbox that’s accessible in Microsoft Exchange Server 2010 or a later version, and in Microsoft Office Outlook Web App.
Users can view an archive mailbox and move or copy messages between their primary mailbox and the archive.
In Exchange 2010 Service Pack 1 (SP1), you can provision a user’s personal archive on the same mailbox database as the user’s primary mailbox, another mailbox database on the same Mailbox server, or a mailbox database on another Mailbox server in either the same or another Active Directory site. This provides flexibility to use tiered storage architecture and to store archive mailboxes on a different storage subsystem, such as near-line storage. In cross-premises Exchange 2010 deployments, you can also provision a cloud-based archive for mailboxes located on your on-premises
QUESTION 32
You have an Exchange Server 2010 organization.
You enable journaling in the organization.
You need to recommend a solution that prevents administrators from reading confidential e-mail messages sent between company executives.
What should you recommend?
A. Deploy Active Directory Rights Management Services (AD RMS) templates and create
Outlook Protection Rules.
B. Deploy Active Directory Rights Management Services (AD RMS) templates and create
Transport Protection Rules.
C. Deploy an X.509 certificate from an enterprise certification authority (CA) to each executive.
Instruct the executive to connect to the Exchange servers by using SMTP over TLS.
D. Deploy an X.509 certificate from a trusted third-party certification authority (CA) to each
executive.
Instruct the executive to encrypt e-mail messages by using Security/Multipurpose Internet
Mail Extensions (S/MIME).
Answer: D
Explanation:
Journal report decryption allows you to save a clear-text copy of IRM-protected messages in journal reports, along with the original, IRM-protected message. If the IRM-protected message contains any supported attachments that were protected by the Active Directory Rights Management Services (AD RMS) cluster in your organization, the attachments are also decrypted.
In Exchange 2010 SP1, members of the Discovery Management role group can access IRM-protected messages returned by a discovery search and residing in a discovery mailbox.
To enable this functionality, use the EDiscoverySuperUserEnabled parameter with Set-IRMConfiguration cmdlet.
http://technet.microsoft.com/en-us/library/dd638140(v=exchg.141).aspx
http://technet.microsoft.com/en-us/library/dd876936(v=exchg.141).aspx
QUESTION 33
Your company has a main office and two branch offices.
Your network consists of a single domain Active Directory forest.
An Active Directory exists for each office.
The main office contains five domain controllers that run windows Server 2004 (x64).
Each branch office contains one read only domain control (RODC) that runs Windows Server 2008.
All domain controllers are configured as global catalog servers.
You plan to deploy one Exchange Server 2010 server in each site.
You need to recommend changes to Active Directory to support the planned deployment.
The solution must ensures that Exchange servers branch office site connect to their local domain controllers.
What should you recommend?
A. Implement a DNS zone for each office.
B. Change all RODCs to Windows Server 2008 (x64) RODCs.
C. Implement a writable domain controller in each branch office.
D. Disable site link bridging for the forest and configure Exchange specific casts.
Answer: C
Explanation:
RODC domain controllers are not considered to be suitable for Exchange Servers.
Microsoft documentation states you must have a writable domain controller to support exchange server
QUESTION 34
Your company has two main offices named Main1 and Main2.
An Active Directory site exists for each office.
Users connect locally to servers in both offices.
The offices connect to each other by using a high speed WAN link.
You plan to deploy Exchange Server 2010.
You need to plan the deployment of Mailbox servers to meet the following requirements:
– Ensure that users can access their mailbox from a server in their site, if a single Mailbox server fails
– Ensure that users can access their mailboxes remotely if a site fails
– Minimize the number of servers
How many Mailbox servers should you include in the plan?
A. 2
B. 3
C. 4
D. 6
Answer: C
Explanation:
You will need 2 servers in each site. This will meet the requirements of the questions.
QUESTION 35
You have an Exchange Server 2010 organization that consists of 50 Exchange Server 2010 servers.
Your company’s security policy states that approved Exchange and Windows Server patches and security updates must be applied to all exchange servers with in one week of being released.
You need to recommend a patch management solution that meets the following requirements:
– Allow administrators to manually approve patches and security updates
– Allow only the installation of approved patches and security updates
– Minimize the administrative effort to deploy patches
– Minimize the deployment casts
What should you include in the solution?
A. Microsoft Update
B. Microsoft System Center Configuration Manager
C. Windows Server Update Services
D. Windows Update
Answer: C
QUESTION 36
You have an Exchange Server 2010 organization.
Your company’s security policy states that only approved mobile devices can connect by using Exchange ActiveSync.
You need to implement a solution that prevents specified mobile devices from connecting to the Exchange servers.
What should you implement?
A. a new client throttling policy
B. a new Exchange ActiveSync device access role
C. a new Exchange ActiveSync policy
D. a new Microsoft Server ActiveSync virtual directory
Answer: B
Explanation:
Allow/Block/Quarantine lists
Accessing the ABQ settings:
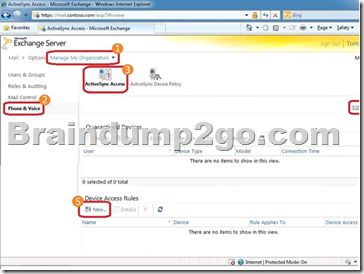
1- Log in to the Exchange Control Panel (ECP)
2- In the ECP, make sure you are managing My Organization (#1 in the screenshot below).
Be aware that most users won’t see the “My Organization” option — it’s only visible to users with Exchange Administrator access.
3- Select Phone & Voice (#2 in the screenshot below) > ActiveSync Access tab (#3 in the screenshot below).
This is the Allow/Block/Quarantine configuration screen.
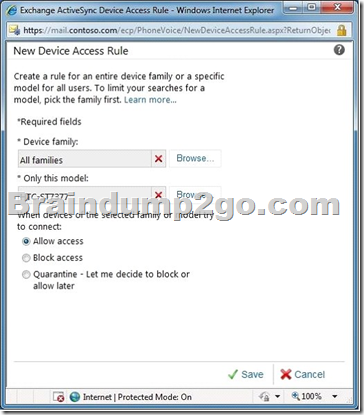
4- Creating a device (or a family of devices) rule: select New from the Device Access Rules section of the ABQ page (#5 in the screenshot above).
Accessing ABQ settings from the Exchange Control Panel
QUESTION 37
You have an Exchange Server 2010 organization.
You need to plan a solution to prevent sensitive information from being forwarded on the Internet.
What should you include in the plan?
A. a custom Send connector
B. custom MailTips
C. Role Based Access Control (RBAC) role entries
D. Transport Protection Rules
Answer: D
Explanation:
Transport protection rules:
When transport protection rules are used with Active Directory Rights Management Services (AD RMS), an administrator can automatically apply Information Rights Management (IRM) protection to e-mail (including Office and XPS attachments) after a message is sent. These rules provide persistent protection to the file no matter where it is sent, internally or externally outside the network, and prevent forwarding, copying, or printing depending on the set of AD RMS policy templates that are available from the AD RMS deployment.
QUESTION 38
Your network contains Exchange Server 2010 servers.
All users access their mailboxes by using Outlook Web App (OWA).
Your company’s compliance policy states the following:
– All e-mail messages that contains customer contracts must be stored for three years
– Users must be able to classify e-mail messages that relate to customer contracts
– Users must be able to move e-mail messages to any folder
You need to recommend a solution that supports the requirements of the compliance policy.
What should you recommend?
A. Managed Folder mailbox policies
B. an OWA mailbox policy
C. Personal Archives and an Archive policy
D. Retention Policy Tags and a Retention Policy
Answer: D
Explanation:
Retention tags are used to apply retention settings to folders and individual items such as e-mail messages and voice mail. These settings specify how long a message remains in a mailbox and the action to be taken when the message reaches the specified retention age. When a message reaches its retention age, it’s moved to the personal archive or deleted.
Unlike managed folders (the MRM feature introduced in Exchange Server 2007), retention tags allow users to tag their own mailbox folders and individual items for retention. Users no longer have to file items in managed folders provisioned by an administrator based on message retention requirements.
You can use retention policies to group one or more retention tags and apply them to mailboxes. A mailbox can’t have more than one retention policy. Retention tags can be linked to or unlinked from a retention policy at any time, and the changes automatically take effect for all mailboxes that have the policy applied.
A retention policy can have the following retention tags:
– One or more RPTs for supported default folders
– One DPT with the Move to Archive action
– One DPT with the Delete and Allow Recovery or Permanently Delete actions
– One DPT for voice mail messages in Exchange 2010 SP1
– Any number of personal tags
Although you can add any number of personal tags to a retention policy, having many personal tags with different retention settings can confuse users. We recommend linking no more than 10 personal tags to a retention policy. Retention policy can contain both archive tags (tags that move items to the personal archive mailbox) and deletion tags (tags that delete items). A mailbox item can also have both types of tags applied. Archive mailboxes don’t have a separate retention policy. The same retention policy is applied to the primary and archive mailbox.
When planning to create retention policies, you must consider whether they’ll include both archive and deletion tags. As mentioned earlier, a retention policy can have one DPT that uses the Move to Archive action and one DPT that uses either the Delete and Allow Recovery or Permanently Delete action. The DPT with the Move to Archive action must have a lower retention age than the DPT with a deletion action. For example, you can use a DPT with the Move to Archive action to move items to the archive mailbox in two years, and a DPT with a deletion action to remove items from the mailbox in seven years.
http://technet.microsoft.com/en-us/library/dd297955.aspx
QUESTION 39
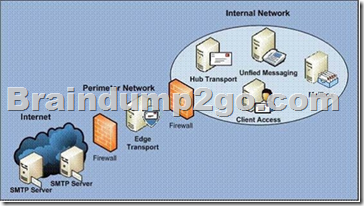
Your network contains an internal network and a perimeter network.
The internal network contains an Active Directory forest.
The forest contains a single domain.
You plan to deploy 10 Edge Transport servers on the perimeter network.
You need to recommend a solution for the Edge Transport server deployment.
The solution must meet the following requirements:
– Allow administrators to apply a single security policy to all Edge Transport servers
– Reduce the administrative overhead that is required to manage servers
– Minimize the attack surface of the internal network
What should you recommend?
A. Implement Network Policy and Access Services (NPAS).
B. Implement Active Directory Federation Services (AD FS).
C. Create a new Active Directory domain in the internal forest and then join all Edge
Transport servers to the new domain.
D. Create an Active Directory forest in the perimeter network and then join all Edge
Transport servers to the new domain.
Answer: D
Explanation:
The Edge Transport Server should be installed on a stand-alone server in a workgroup or as a domain member in an Active Directory dedicated to servers located in the perimeter network:
The first time EdgeSync replication occurs, the ADAM store is populated, and after that data from Active Directory is replicated at fixed intervals.
You can specify the intervals or use the default settings, which when speaking configuration data is every hour and every 4th hour for recipient data.
QUESTION 40
You have an Exchange Server 2010 organization.
Company policy states that a copy of user’s mailbox must be kept for one year after the user leaves the company.
All user accounts are in an organizational unit (OU) named OU1.
A compliance administrator plans to export the mailboxes to personal folders.
You need to recommend a solution that allows the compliance administrator to meet the requirements of the company policy.
What should you include in the solution?
A. a new management role assignment
B. delegated perimeters to OU1
C. managed folder mailbox policies
D. new personal Archives
Answer: A
Explanation:
By default, the Mailbox Import Export management role isn’t included in any of the built-in role groups, such as the Organization Management role group. To import or export mailbox data, you need to add the Mailbox Import Export management role to a user or a role group
New-ManagementRoleAssignment -Role “Mailbox Import Export” -User “<username>” Another way of doing this is creating an Active Directory group and adding permissions to this group using the following command:
New-ManagementRoleAssignment -Role “Mailbox Import Export” -Group “<usergroup>” When you are done, you will only have to add users to this group to allow them to export and import mailboxes.
Mailbox export request is processed by the Client Access server role. Because multiple Client Access servers can exist in a site the request could be processed by any one of them. To ensure that the path to the export PST file is valid for any Client Access server it has to be a UNC path to network share, not a local path To export a mailbox to PST you use New-MailboxExportRequest cmd:
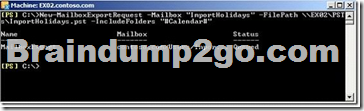
A management role assignment policy is a collection of one or more end-user management roles that enables end users to manage their own Microsoft Exchange Server 2010 mailbox and distribution group configuration. Role assignment policies, which are part of the Role Based Access Control (RBAC) permissions model in Exchange 2010, enable you to control what specific mailbox and distribution group configuration settings your end users can modify. Different groups of users can have role assignment policies specialized to them.
http://technet.microsoft.com/en-us/library/dd638100.aspx
Braindump2go New Published Exam Dumps: Microsoft 70-663 Practice Tests Questions, 291 Latest Questions and Answers from Official Exam Centre Guarantee You a 100% Pass! Free Download Instantly!
FREE DOWNLOAD: NEW UPDATED 70-663 PDF Dumps &70-663 VCE Dumps from Braindump2go: http://www.braindump2go.com/70-663.html (291 Q&As)