Do you want to pass Microsoft 70-689 Exam ? If you answered YES, then look no further. Braindump2go offers you the best 70-689 exam questions which cover all core test topics and certification requirements. All REAL questions and answers from Microsoft Exam Center will help you be a 70-689 certified!
Vendor: Microsoft
Exam Code: 70-689
Exam Name: Microsoft Upgrading Your Skills to MCSA Windows 8.1
QUESTION 151
Drag and Drop Questions
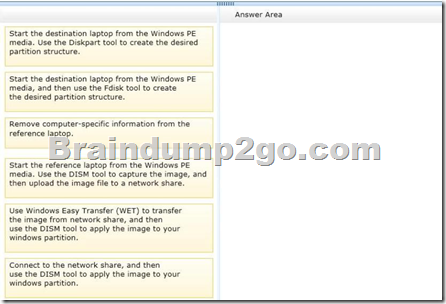
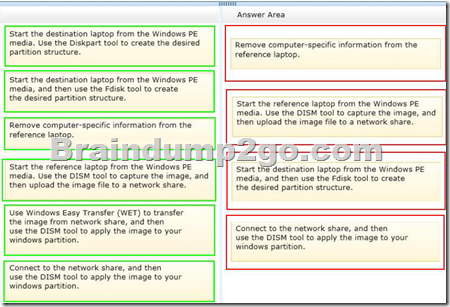
Your company recently purchased 25 new laptops.
All 25 laptops have the same hardware configuration and do not have any operating system installed.
You have been asked to deploy Windows 8 on these laptops.
You have installed and configured Windows 8 on a reference laptop.
You need to create an image and deploy it to the 25 new laptops.
Which four actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
Answer:
Explanation:
Note:
– You can create a reference computer by deploying Windows, and then removing the computer-specific information from the system.
– On the destination computer, you will create a structure for the partitions where you apply your images. The partition structure on the destination computer must match the partition structure of the reference computer.
– Use the Diskpart tool and the DISM tool to apply Windows images to one or more partitions onto a computer for deployment.
– Use the DISM tool to apply images to your Windows partition.
Reference: How to Capture Images of Hard Disk Partitions by Using DISM
Reference: How to Apply Images by Using DISM
QUESTION 152
You have Windows 8.1 Pro client computers.
You need to recommend a solution to roll back the Windows Defender engine and the malware signature files on the computers.
The solution must minimize administrative effort.
What should you include in the recommendation?
A. the Program and Features Control Panel item
B. the Reset your PC push-button reset feature
C. System Restore points
D. the Refresh your PC push-button reset feature
Answer: C
Explanation:
Restore System to a Previous State Using Restore Point Restoring your Windows operating system to a previous state is nothing new, but this feature can be very handy and time saving. For example, if you installed a new application or driver and your system starts to behave abnormally, or if your computer is infected by a virus from one unintentional mouse click on a link, wherever the case may be, you may want to go back to a previous state, say yesterday.
You can refresh or reset your system, but system restore is your best bet for this kind of scenarios.
QUESTION 153
Drag and Drop Questions
You administer computers that run windows 7 and Windows 8.
You run an application that saves files that contain local settings unique to each user.
You want to allow users to synchronize settings for an application to any enterprise computer when they log on to the enterprise computer.
You need to implement a solution that will move a user’s settings files to any computer.
You also need to ensure that you can roll back the changes if necessary.
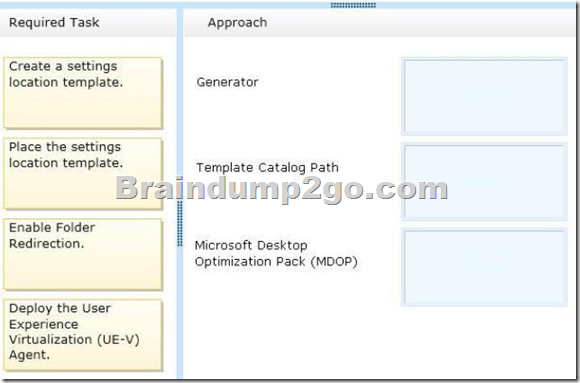
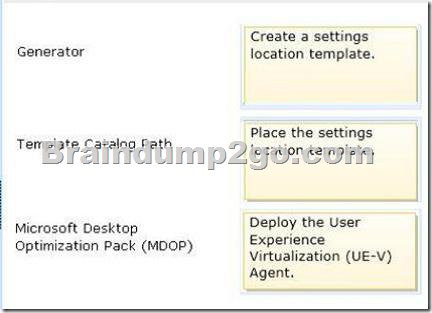
Which required task or tasks should you perform with each approach? (To answer, drag the appropriate required task to the corresponding approach. Each required task may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
Answer:
Explanation:
– Microsoft User Experience Virtualization (UE-V) uses settings location templates to roam application settings between user computers.
Some standard settings location templates are included with User Experience Virtualization.
You can also create, edit, or validate custom settings location templates with the UE-V Generator.
– Settings template catalog
The User Experience Virtualization settings template catalog is a folder path on UE-V computers or a Server Message Block (SMB) network share that stores all the custom settings location templates. The UE-V agent retrieves new or updated templates from this location.
The UE-V agent checks this location once each day and updates its synchronization behavior based on the templates in this folder. Templates that were added or updated in this folder since the last time that the folder was checked are registered by the UE-V agent.
The UE-V agent deregisters templates that are removed from this folder.
By default, templates are registered and unregistered one time per day at 3:30 A.M.
local time by the task scheduler.
– The Microsoft Desktop Optimization Pack (MDOP) is a suite of technologies available as a subscription for Software Assurance customers.
MDOP virtualization technologies help personalize the user experience, simplify application deployment, and improve application compatibility with the Windows operating system (UE-V/App-V/MED-V).
Additionally, MDOP helps manage, monitor, and deploy key Windows features (MBAM/AGPM). Using MDOP shifts desktop repair from reactive to proactive, saving time and removing challenges associated with troubleshooting and repairing system failures (DaRT).
Reference: Create UE-V Settings Location Templates with the UE-V Generator
QUESTION 154
Drag and Drop Questions
You support a computer that runs Windows 8 Enterprise.
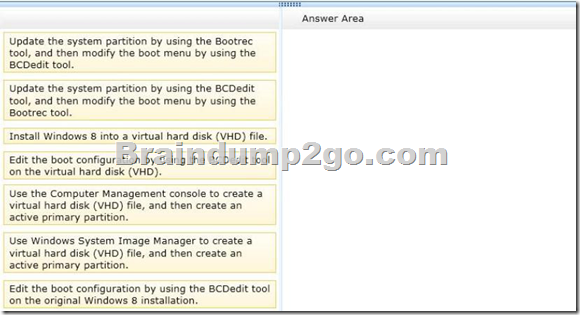
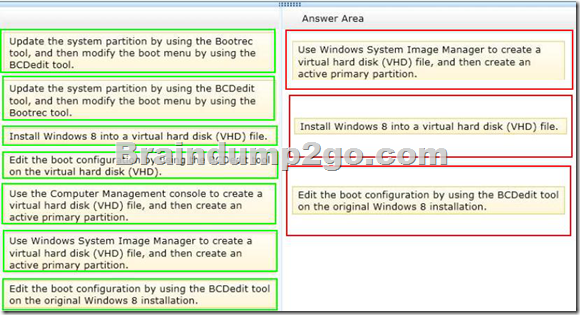
You want to create a dual-boot configuration by using the native boot virtual hard disk (VHD) method.
You need to create an alternate Windows 8 installation.
Which three actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
Answer:
QUESTION 155
Drag and Drop Questions
You support computers that run Windows 8 Enterprise.
Company policy requires that Microsoft Internet Explorer be the only browser allowed and supported.
You collect software metering data and discover that several users are running other third-party browsers.
You need to block other web browsers from running on the computers.
All other applications should be allowed.
Which three actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
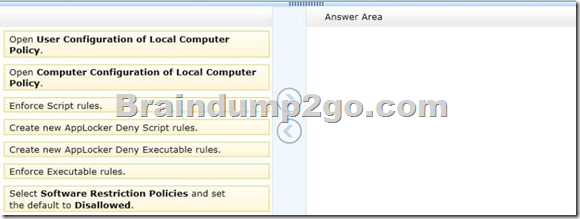
Answer:
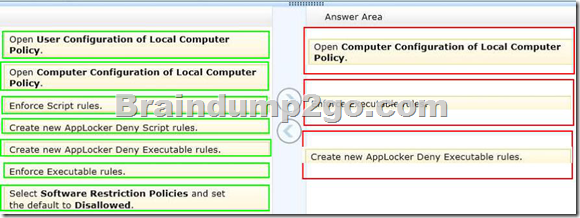
Explanation:
– Use Computer Configuration (not user configuration).
– Restrict Access to Programs with AppLocker in Windows 7 If you share a computer and don’t want other users accessing certain applications, there is a new feature in Windows 7 that allows you to block them. We restrict what programs other users can access using AppLocker.
Under Local Computer Policy go to Computer Configuration \ Windows Settings \ Security Settings \ Application Control Policies \ AppLocker.
Now under AppLocker Properties check the boxes next to Configured under Executable rules then click Ok.
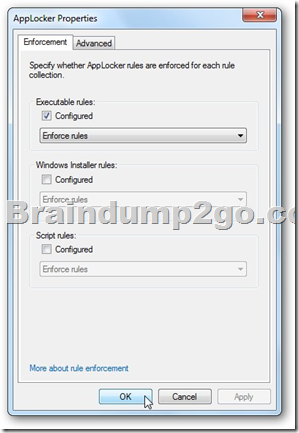
Finally create a Deny Executable rule for each browser you want to block.
QUESTION 156
Drag and Drop Questions
You support computers that run windows 8 Enterprise.
AppLocker policies are deployed. Company policy states that AppLocker must be disabled.
You need to disable AppLocker.
Which three actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
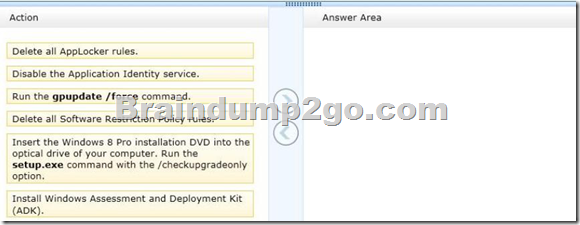
Answer:
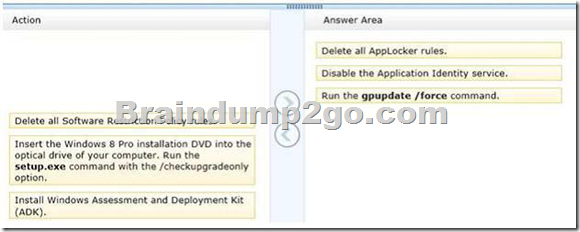
Explanation:
– Before you can enforce AppLocker policies, you must start the Application Identity service by using the Services snap-in console.
– The Application Identity service determines and verifies the identity of an application. Stopping this service will prevent AppLocker policies from being enforced.
QUESTION 157
Drag and Drop Questions
You administer laptops and virtual desktop computers that run Windows 8 and are joined to an Active Directory domain.
Your company provides virtual desktop computers to all users. Employees in the sales department also use laptops, sometimes connected to the company network and sometimes disconnected from the company network.
You want sales department employees to have the same personal data, whether they are using their virtual desktop computers or their laptops.
You need to configure the network environment to meet the requirements.
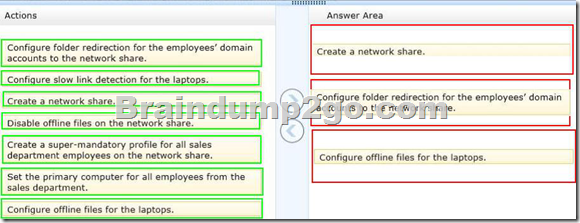
Which three actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
Answer:
Explanation:
Folder Redirection and Offline Files are used together to redirect the path of local folders (such as the Documents folder) to a network location, while caching the contents locally for increased speed and availability.
– Folder Redirection enables users and administrators to redirect the path of a known folder to a new location, manually or by using Group Policy. The new location can be a folder on the local computer or a directory on a file share. Users interact with files in the redirected folder as if it still existed on the local drive. For example, you can redirect the Documents folder, which is usually stored on a local drive, to a network location. The files in the folder are then available to the user from any computer on the network.
– Offline Files makes network files available to a user, even if the network connection to the server is unavailable or slow. When working online, file access performance is at the speed of the network and server. When working offline, files are retrieved from the Offline Files folder at local access speeds. A computer switches to Offline Mode when:
The new Always Offline mode has been enabled
The server is unavailable
The network connection is slower than a configurable threshold
The user manually switches to Offline Mode by using the Work offline button in Windows Explorer Reference: Folder Redirection, Offline Files, and Roaming User Profiles overview
QUESTION 158
You manage a network that includes computers that run Windows 8 Enterprise.
All of the computers on the network are members of an Active Directory domain.
The company recently proposed a new security policy that prevents users from synchronizing applications settings, browsing history, favorites, and passwords from the computers with their Microsoft accounts.
You need to enforce these security policy requirements on the computers.
What should you do?
A. From each computer, navigate to Change Sync Settings and set the Sync Your Settings
options for Apps, Browser, and Passwords to Off.
B. On the Group Policy Object, configure the Accounts: Block Microsoft accounts Group Policy
setting to Users can’t add or log on with Microsoft accounts.
C. On the Group Policy Object, configure the Accounts: Block Microsoft accounts Group Policy
setting to Users can’t add Microsoft accounts.
D. From each computer, navigate to Change Sync Settings and set the Sync Your Settings
option to Off.
Answer: B
QUESTION 159
You administer a computer that runs Windows 8 Pro.
You need to create a backup copy of the computer system drive.
The backup copy must support a complete system drive restore to another computer.
What should you do?
A. Create a system restore point.
B. Run the bcdedit /export command.
C. Perfom a backup to a shared folder by using the wbadmin command with the-allcritical
switch.
D. Create a system recovery drive.
Answer: C
Explanation:
– allCritical
Specifies that all critical volumes (volumes that contain operating system’s state) be included in the backups.
This parameter is useful if you are creating a backup for bare metal recovery.
It should be used only when -backupTargets specified, otherwise the command will fail.
Can be used with the -include option.
http://technet.microsoft.com/en-us/library/cc742083(v=ws.10).aspx
QUESTION 160
You manage client computers that run Windows 8 and are part of a workgroup.
These computers are configured to use Microsoft Update.
Updates are downloaded every day at 10:00 and installed automatically.
Users report that their computers sometimes reboot without any interaction.
You need to prevent unplanned automatic reboots of the computers.
What should you do?
A. Enable the Reschedule Automatic Updates scheduled installations policy setting.
B. Disable the Re-prompt for restart with scheduled installations policy setting.
C. Enable the Automatic Updates detection frequency policy setting.
D. Enable the No auto-restart with logged on users for scheduled automatic updates installations
policy setting.
Answer: A
70-689 Updated Questions are 2015 Latest Released Which 100% will Meet in Your 70-689 Test! Braindump2go New Released 70-689 Exam Dumps Contain All New Added Questions Which Will Help you Have A Totally Success in 2015 New Tear! Download our 100% Pass Guaranteed 70-689 Exam Dumps Full Version, special 10% Off Discount enjoyed!