Real Latest 74-409 Exam Questions Updated By Official Microsoft Exam Center! Braindump2go Offers 74-409 Dumps sample questions for free download now! You also can visit our website, download our premium Microsoft 74-409 Exam Real Answers, 100% Exam Pass Guaranteed!
Vendor: Microsoft
Exam Code: 74-409
Exam Name: Server Virtualization with Windows Server Hyper-V and System Center
Keywords: Microsoft 74-409 Exam Dumps,74-409 Practice Tests,74-409 Practice Exams,74-409 Exam Questions,74-409 PDF,74-409 VCE,74-409 Training Guide,74-409 Study Material,74-409 Book
QUESTION 71
A company uses System Center 2012 R2 Operations Manager and System Center 2012 R2 Virtual Machine Manager (VMM).
You need to provide a detailed overview of the fabric that services the company’s private clouds.
What should you do?
A. Import the Management Pack for System Center 2012 R2 VMM Fabric Dashboard.
B. Use the System Center Global Service Monitor as part of the monitoring strategy.
C. Import the Management Pack for System Center 2012 Service Manager.
D. Use the Windows Intune service as part of the monitoring strategy.
Answer: A
Explanation:
http://www.networkworld.com/community/blog/whats-new-operations-managersystem-center 2012-r2
Fabric Monitoring
A close integration between System Center 2012 R2 Virtual Machine Manager and System
Center 2012 R2 Operations Manager introduces System Center cloud monitoring of virtual layers for private cloud environments. To get this new functionality, use the System Center 2012 Management Pack for System Center 2012 R2 Virtual Machine Manager Dashboard, which is imported automatically when you integrate Operations Manager and Virtual Machine Manager. For information about how to integrate Operations Manager and Virtual Machine Manager, see Configuring Operations Manager Integration with VMM.
QUESTION 72
Hotspot Question
A company has a Windows Server 2012 R2 Hyper-V environment that contains a single Active Directory Domain Services domain named Contoso.com.
The environment also has three servers named Host1, Host2, and Host3 that have the Hyper-V role installed.
You configure all of the hosts as a single failover cluster.
You have two guest clusters named VM-Cluster1 and VM-Cluster2.
The environment is configured as shown in the following diagram:
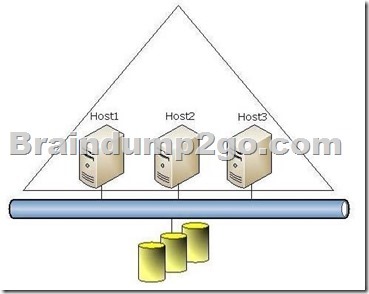
When a virtual machine guest cluster node is migrated to another host, the guest cluster fails over to the other node.
You must provide high availability for all virtual machines.
Guest clusters must NOT fail over if they are migrated to another host.
You need to configure the guest clusters.
Use the drop-down menus to complete each statement based on the information presented in the screenshot. Each correct selection is worth one point.
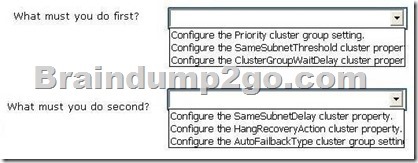
Answer:
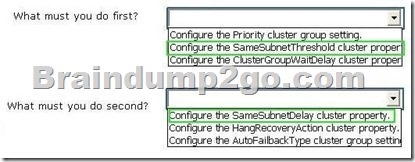
Explanation:
http://technet.microsoft.com/en-us/library/dn440540.aspx
Protect against short-term network interruptions
Failover cluster nodes use the network to send heartbeat packets to other nodes of the cluster. If a node does not receive a response from another node for a specified period of time, the cluster removes the node from cluster membership. By default, a guest cluster node is considered down if it does not respond within 5 seconds. Other nodes that are members of the cluster will take over any clustered roles that were running on the removed node.
Typically, during the live migration of a virtual machine there is a fast final transition when the virtual machine is stopped on the source node and is running on the destination node. However, if something causes the final transition to take longer than the configured heartbeat threshold settings, the guest cluster considers the node to be down even though the live migration eventually succeeds. If the live migration final transition is completed within the TCP time-out interval (typically around 20 seconds), clients that are connected through the network to the virtual machine seamlessly reconnect.
To make the cluster heartbeat time-out more consistent with the TCP time-out interval, you can change the SameSubnetThreshold and CrossSubnetThreshold cluster properties from the default of 5 seconds to 20 seconds. By default, the cluster sends a heartbeat every 1 second. The threshold specifies how many heartbeats to miss in succession before the cluster considers the cluster node to be down.
QUESTION 73
A company has one central data center and five branch offices.
Each office has three Hyper-V host servers that run Windows Server 2012 R2 Datacenter edition. Each branch office has a system administrator.
You plan to deploy virtual machines (VMs) that run Windows Server 2012 R2 Standard edition to each branch office.
You have the following requirements:
– The VMs must be activated at the branch offices, even if the branch office has no Internet connectivity.
– Activation keys must NOT be shared with the branch office administrators.
– You must be able to track license usage from the central location, even without access rights to the VMs.
– You must be able to verify license compliance and perform real time reporting on license usage from a central location.
You need to configure licensing and activation for the VMs.
Which feature or tool should you use?
A. Multiple Activation Key (MAK)
B. Volume Activation Management Tool (VAMT)
C. Key Management Service (KMS)
D. Automatic Virtual Machine Activation (AVMA)
Answer: D
Explanation:
http://technet.microsoft.com/en-us/library/dn303421.aspx
Automatic Virtual Machine Activation (AVMA) acts as a proof-of-purchase mechanism, helping to ensure that Windows products are used in accordance with the Product Use Rights and Microsoft Software License Terms.
AVMA lets you install virtual machines on a properly activated Windows server without having to manage product keys for each individual virtual machine, even in disconnected environments.
AVMA binds the virtual machine activation to the licensed virtualization server and activates the virtual machine when it starts up.
AVMA also provides real-time reporting on usage and historical data on the license state of the virtual machine.
Reporting and tracking data is available on the virtualization server.
QUESTION 74
Drag and Drop Question
A company has a Hyper-V host server that runs Windows Server 2012 R2 Datacenter edition. The host server has a Generation 2 virtual machine (VM) that runs Windows Server 2012 R2 Standard edition.
The drive that contains the VM system partition is at 90 percent of its capacity.
You have the following requirements:
– The VM must continue to run during any system maintenance activities.
– You must use the least amount of administrative effort to accomplish the task.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
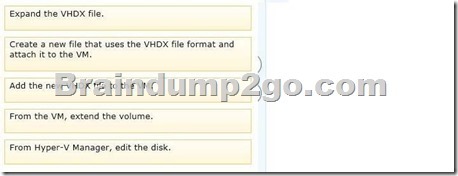
Answer:

Explanation:
We can also assume that the vhdx file is connected to a virtual SCSI controller because it’s a Gen 2 VM. This is a prereq to online vhdx resizing
http://technet.microsoft.com/en-us/library/dn282284.aspx
BEST answer is :
From Hyper-V Manager, edit the disk
Expand the VHDX file
From the VM, extend the volume
QUESTION 75
You have a Windows Server 2012 R2 Hyper-V environment that includes System Center 2012 R2 Virtual Machine Manager (VMM).
The environment includes five physical servers.
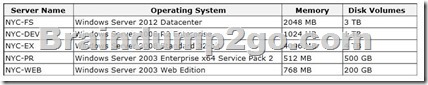
The servers are configured as follows:
You plan to use VMM to migrate physical machines to virtual machines.
You must migrate all servers that support physical to virtual (P2V) migration.
You need to migrate the servers.
Which three servers should you migrate? Each correct answer presents part of the solution.
A. NYC-WEB
B. NYC-PR
C. NYC-DEV
D. NYC-FS
E. NYC-EX
Answer: ABC
Explanation:
The source computer cannot have any volumes larger than 2040 GB.
This disqualifies NYCFS( not D) and NYC-EX (not E).
Note:
– Requirements on the Source Machine To perform a P2V conversion, your source computer:
– Must have at least 512 MB of RAM.
– Cannot have any volumes larger than 2040 GB.
– Must have an Advanced Configuration and Power Interface (ACPI) BIOS Vista WinPE will not install on a non-ACPI BIOS.
– Must be accessible by VMM and by the host computer.
– Cannot be in a perimeter network.
–> A perimeter network, which is also known as a screened subnet, is a collection of devices and subnets placed between an intranet and the Internet to help protect the intranet from unauthorized Internet users. The source computer for a P2V conversion can be in any other network topology in which the VMM server can connect to the source machine to temporarily install an agent and can make Windows Management Instrumentation (WMI) calls to the source computer.
– The source computer should not have encrypted volumes.
–> If the source computer has encrypted volumes, an offline P2V conversion may render the computer unbootable.
Answer: So based on the prerequisites, NYC-FS, NYC-EX and NYC-PR needs to be reconfigured
UPDATE:
As of System Center 2012 R2, you can no longer perform P2V conversions in VMM.
For information about how to use an earlier version of Virtual Machine Manager to mitigate this change, see the:
“How to perform a P2V in a SCVMM 2012 R2 environment blog” –
http://blogs.technet.com/b/scvmm/archive/2013/10/03/how-to-perform-a-p2v-in-a-scvmm-2012-r2-environment.aspx
http://technet.microsoft.com/en-us/library/hh427293.aspx
QUESTION 76
Drag and Drop Question
A software company has a Windows Server 2012 R2 server that has the Hyper-V role installed. The server hosts a single virtual machine (VM) named VM1.
VM1 has one virtual CPU, one virtual hard disk, and one virtual network interface card (NIC) that is attached to an external network.
The company prepares to test its software in VM1.
Before testing begins, VM1 must meet the following requirements:
– Availability of network bandwidth must be maximized.
– VM network connectivity must be fault tolerant.
You need to configure the environment.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
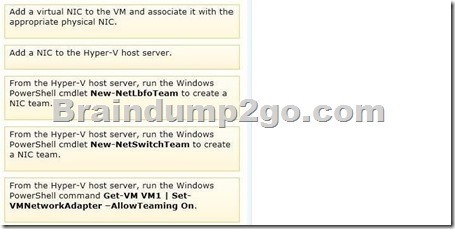
Answer:
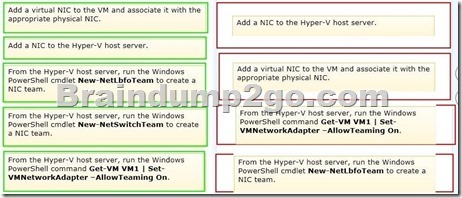
Explanation:
Set-VMNetworkAdapter
http://technet.microsoft.com/en-us/library/hh848457.aspx
AllowTeaming
Specifies whether the virtual network adapter can be teamed with other network adapters connected to the same virtual switch. The value can be On (allowed) or Off (disallowed).
New-NetLbfoTeam
http://technet.microsoft.com/en-us/library/jj130847.aspx
-The New-NetLbfoTeam cmdlet creates a new NIC team that consists of one or more network adapters. Teaming network adapters of different speeds is not supported. You can create a team with network adapters of different speeds, but the network traffic distribution algorithms do not take the speed of each network adapter into consideration when distributing traffic.
-When you create a team, you can specify additional properties such as TeamingMode and LoadBalancingAlgorithm.
-You need administrator privileges to use New-NetLbfoTeam.
New-NetSwitchTeam
http://technet.microsoft.com/en-us/library/jj553814.aspx
he New-NetSwitchTeam cmdlet creates a new switch team. A switch team must have a name for the team and must be created with one or more members, or network adapters.
The network switch team is a team that is controlled by a Hyper-V extensible switch forwarding extension. No other cmdlets can be used to manage a switch team and the NetSwitchTeam cmdlets must not be used to manage standard, or non-switch, network adapter teams.
QUESTION 77
Hotspot Question
You are the virtuaiization administrator for an organization.
You use System Center 2012 R2 Virtual Machine Manager (VMM) to configure a virtual machine (VM) template that will host a new application.
You have the following requirements for new VMs that host the application:
– New VMs must be highly available.
– You must join the VMs to an Active Directory Domain Services domain at deployment.
You need to modify the VM template to support the requirements.
On the properties page for the template, which two settings should you configure? To answer, select the appropriate settings in the answer area.
Answer:
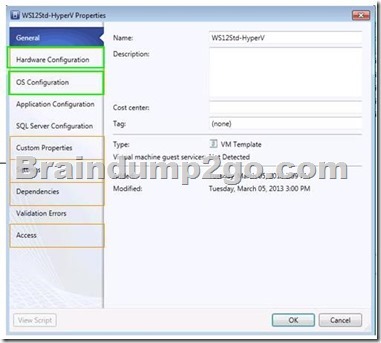
Explanation:
http://technet.microsoft.com/en-us/library/hh427282.aspx
QUESTION 78
Drag and Drop Question
A company has one Active Directory Domain Services (AD DS) forest that contains two domains. The company has a Hyper-V environment that runs Windows Server 2012 R2.
The company also has two virtual machines (VMs) that run Windows Server 2012.
The VMs are NOT part of a domain.
You plan to deploy a guest cluster by using a shared virtual hard disk (VHDX).
You must use native disk support that is included in the Failover Clustering feature.
The compliance department requires that you perform as many tasks as possible you’re your domain account for auditing purposes.
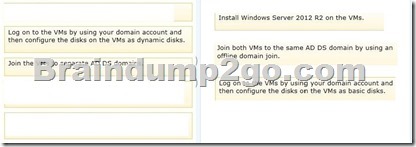
You need to prepare to create the guest cluster.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
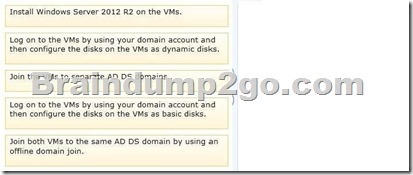
Answer:
QUESTION 79
An organization has two teams of developers.
One team develops web applications.
The other team develops mobile applications.
You administer servers for the organization.
All four servers run Windows Server 2012 R2 and are part of a Hyper-V cluster.
You create six virtual machines (VMs) for each team.
You plan to create a virtual environment for the teams.
You have the following requirements:
– Both teams must use the 10.10.10.0/24 subnet.
– Each VM for the web application team must have network connectivity with all other web application VMs.
– Each VM for the mobile application team must have network connectivity with all other mobile application VMs.
– The VMs for the web application team must NOT connect to the VMs for the mobile application team.
You need to create the network for the VMs.
What should you do?
A. Configure one connected network.
Allow new VM networks created on this logical network to use network virtualization.
B. Set the virtual LAN ID for the management network.
C. Enable private virtual LAN (PVLAN) networks.
D. Configure one connected network.
Do NOT allow new VM networks created on this logical network to use network virtualization.
Answer: A
Explanation:
http://blogs.technet.com/b/scvmm/archive/2013/06/17/logical-networks-part-v-network-virtualization.aspx’ where it states:
“Network Virtualization introduced in Windows Server 2012 Hyper-V provides administrators with the ability to create multiple virtual networks on a shared physical network. In this approach to isolation, each tenant gets a complete virtual network, which includes support for virtual subnets and virtual routing. Tenants can even use their own IP addresses and subnets in these virtual networks, even if these conflict with or overlap with those used by other tenants. Further, since virtual networks are defined entirely in software, it is not necessary to reconfigure the physical network (unlike VLANs and PVLANS solutions) to onboard or remove tenant networks or to make changes to reflect new business requirements.”
QUESTION 80
Drag and Drop Question
A company has a single-domain Active Directory Domain Services (AD DS) environment.
Some servers and all domain controllers are deployed on the internal network.
All servers in the perimeter network are joined to a workgroup.
The company uses System Center 2012 R2 Operations Manager to monitor the server infrastructure on the internal network.
The company plans to use Audit Collection Services (ACS) for one Internet Information Services (IIS) server that is in the perimeter network.
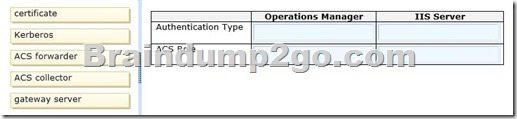
You need to configure the authentication type and ACS role for Operations Manager and the IIS server.
How should you configure the servers? To answer, drag the appropriate authentication type and ACS role to the location or locations in the answer area. Each authentication type and ACS role may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Answer: 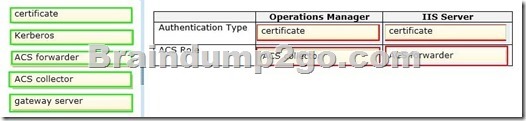
Explanation:
How to Configure Certficates for ACS Collector and Forwarder
http://technet.microsoft.com/en-us/library/hh872886.aspx
When the Audit Collection Service (ACS) Forwarder is located in a domain separate from the domain where the ACS Collector is located, and no two-way trust exists between the two domains, certificates must be used so that authentication can take place between the ACS Forwarder and the ACS Collector.
Braindump2go New Released 74-409 Dump PDF Free Download, 105 Questions in all, Passing Your Exam 100% Easily!