Braindump2go New Released Microsoft 70-689 Practice Tests Sample Questions Free Download! 100% Same Questions with Actual 70-689 Exam! Guaranteed 100% Pass!
Vendor: Microsoft
Exam Code: 70-689
Exam Name: Microsoft Upgrading Your Skills to MCSA Windows 8.1
QUESTION 161
Hotspot Questions
You support desktop computers that run Windows 8 Enterprise.
One computer is a member of a workgroup and is used as a guest computer in a reception area.
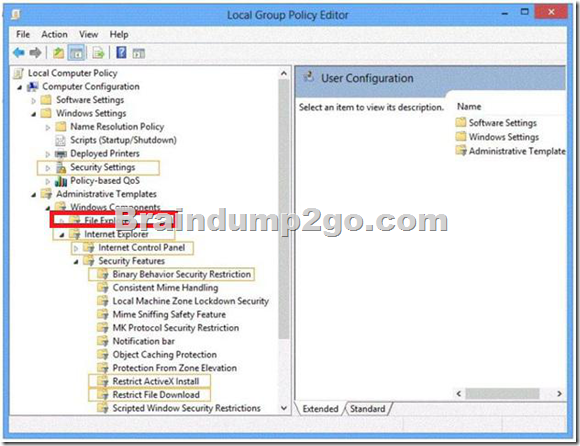
You need to configure the SmartScreen setting to require administrator approval before running downloaded unknown software on the desktop computer.
Which policy setting should you use? (To answer, select the appropriate object in the answer area.)
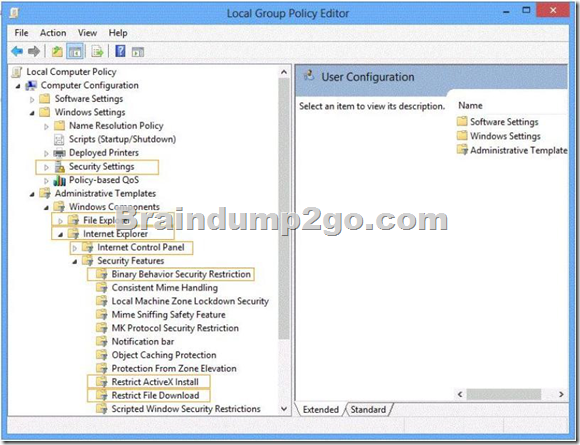
Answer:
QUESTION 162
You administer computers that run Windows 8 Pro.
Your company uses credit card readers that require a custom driver supplied by the manufacturer.
The readers frequently are moved from computer to computer.
Your company recently purchased five new computers that run Windows 8 Pro.
You want the required drivers to be installed automatically and silently when users connect the readers to the new computers.
You need to pre-stage the credit card reader driver on the new computers.
What should you do?
A. Add a Registry key with a path to a network shared folder that has the driver installation files.
B. Run the pnputil.exe utility.
Specify the document scanner driver.
C. Add a Registry key with a path to a local folder on every computer.
Copy the driver installation files to the folder.
D. Run the dism.exe utility.
Copy the driver files to the C:\Windows\System32\drivers folder in the WIM image.
Answer: B
QUESTION 163
You support computers that run Windows 8 Enterprise.
Your company protects all laptops by using the BitLocker Network Unlock feature.
Some employees work from home.
You need to ensure that employees can log on to their laptops when they work from home.
What should you do?
A. Provide employees their BitLocker PINs.
B. Ensure that the Trusted Platform Module (TPM) chips in the laptops are version 1.2 or greater.
C. Enable BitLocker To Go.
D. Have users run the Manage-bde.exe-unlock command before they disconnect from the
company network.
Answer: A
Explanation:
Original answer was `A’ but, this would require an elevated command prompt.
What is a BitLocker Drive Encryption startup key orPIN?
Reference:
http://windows.microsoft.com/en-US/windows-vista/What-is-a-BitLocker-Drive-Encryption-startup-key-or-PIN
In addition to the option of creating a startup key, you have the option of creating a startup personal identification number (PIN).
You can create either the startup key or the startup PIN, but not both.
The startup PIN can be any number that you choose from 4 to 20 digits in length.
The PIN is stored on your computer.
You will have to type the PIN each time you start the computer.
QUESTION 164
Drag and Drop Questions
You administer computers and printers on your company network.
The computers run Windows 8 Pro.
You need to remove a print job from a print queue by using a remote PowerShell session.
Which three commands should you run in sequence? (To answer, move the appropriate commands from the list of commands in the answer area and arrange them in the correct order.)
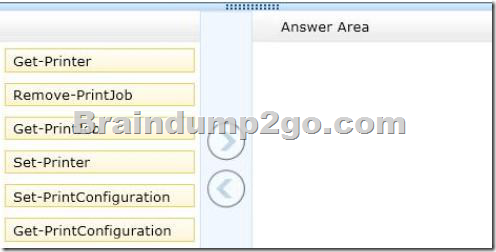
Answer:
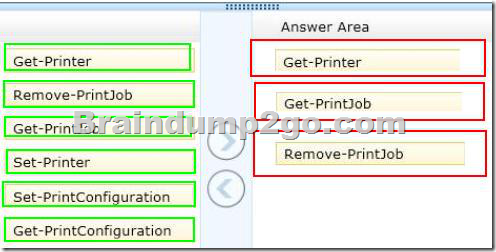
Explanation:
– The Get-Printer cmdlet retrieves a list of printers installed on a computer.
You can also use Get-Printer to retrieve the properties of a single printer, and then use that information as input into other cmdlets.
– Get-PrintJob
Retrieves a list of print jobs in the specified printer.
The Get-PrintJob cmdlet retrieves the current print jobs in the specified printer.
Use the PrinterName parameter to list the print jobs from the specified printer.
– Remove-PrintJob
Removes a print job on the specified printer.
Reference: Get-Printer; Get-PrintJob; Remove-PrintJob
QUESTION 165
You administer Windows 8 Pro and Windows RT tablets for your company.
Your company network includes a Windows Server 2012 domain and Microsoft Exchange 2010 with ActiveSync and Outlook Web Access.
Users will be using the tablets outside of the corporate network.
The Microsoft Exchange ActiveSync policy is configured to require an alphanumeric password.
You need to ensure an alphanumeric password is required on all Windows 8 tablets.
What should you do?
A. From the Mail app, add the user’s Exchange account.
B. Set up New Partnership in Sync Center.
C. From Sync your Settings, set Password to Off.
D. Create a user profile by using a Microsoft account.
Answer: A
QUESTION 166
Drag and Drop Questions
You administer computers that run Windows 8.
The computers on your network are produced by various manufacturers and often require custom drivers.
You need to design a recovery solution that allows the repair of any of the computers by using a Windows Recovery Environment (WinRE).
In which order should you perform the actions? (To answer, move all actions from the list of actions to the answer area and arrange them in the correct order.)
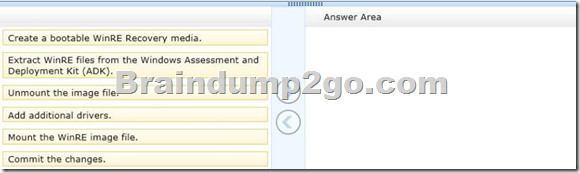
Answer:
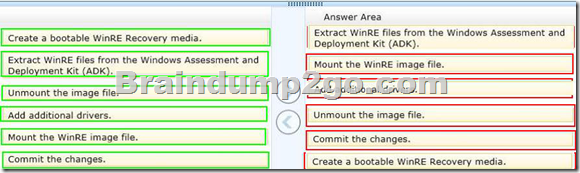
Explanation:
– The Windows Assessment and Deployment Kit (Windows ADK) is a collection of tools and documentation that you can use to customize, assess, and deploy Windows operating systems to new computers.
– Walkthrough: Create a Custom Windows PE Image
Step 1: Set Up a Windows PE Build Environment
Step 2: Mount the Base Windows PE Image
Step 3: Add Boot-Critical Drivers
Step 4: Add Optional Components
Step 5: Add Language Support (Optional)
Step 6: Add More Customization (Optional)
Step 7: Commit Changes
– Walkthrough: Create a Windows RE Recovery Media
Step 1: Create a Windows RE Image
Step 2: Create a bootable media
Reference: Walkthrough: Create a Custom Windows PE Image
Walkthrough: Create a Windows RE Recovery Media
QUESTION 167
You support computers that run Windows 8 and are members of an Active Directory domain. Recently, several domain user accounts have been configured with super-mandatory user profiles.
A user reports that she has lost all of her personal data after a computer restart.
You need to configure the user’s computer to prevent possible user data loss in the future.
What should you do?
A. Configure the user’s documents library to include folders from network shares.
B. Remove the .man extension from the user profile name.
C. Add the .dat extension to the user profile name.
D. Configure Folder Redirection by using the domain group policy.
Answer: D
Explanation:
A mandatory user profile is a special type of pre-configured roaming user profile that administrators can use to specify settings for users. With mandatory user profiles, a user can modify his or her desktop, but the changes are not saved when the user logs off. The next time the user logs on, the mandatory user profile created by the administrator is downloaded.
There are two types of mandatory profiles: normal mandatory profiles and super mandatory profiles. User profiles become mandatory profiles when the administrator renames the NTuser.dat file (the registry hive) on the server to NT user.man.
The .man extension causes the user profile to be a read-only profile.
User profiles become super-mandatory when the folder name of the profile path ends in .man;
for example, \\server\share\mandatoryprofile.man\.
Super-mandatory user profiles are similar to normalmandatory profiles, with the exception that users who have super-mandatory profiles cannot log on when the server that stores the mandatory profile is unavailable. Users with normal mandatory profiles can log on with the locally cached copy of the mandatory profile.
Only system administrators can make changes to mandatory user profiles. http://msdn.microsoft.com/en-us/library/windows/desktop/bb776895(v=vs.85).aspx
QUESTION 168
Hotspot Questions
You have a computer that runs Windows 8 Enterprise.
You need to ensure that all users can see the history of detected items in Windows Defender. Which option on the Settings tab should you select? (To answer, select the appropriate option in the answer area.)
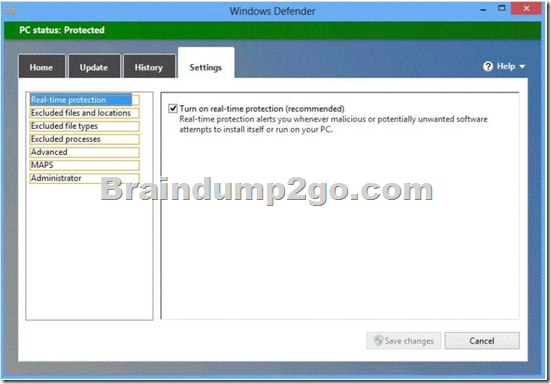
Answer:

QUESTION 169
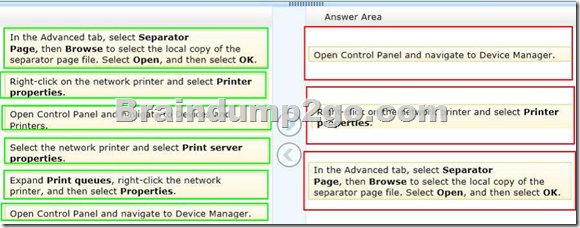
Drag and Drop Questions
You administer computers and printers on your company network.
The computers run Window 8 Pro.
An employee wants to add a separator page to her printer task on a network printer.
You create a separator page file and save it to the C:\Windows\System32 folder on her computer.
You need to configure the computer to use the separator page for the print task.
Which three actions should you perform in sequence on the computer? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
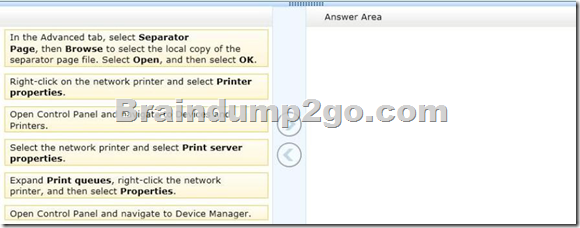
Answer:
QUESTION 170
You are an IT consultant for small and mid-sized businesses.
One of your clients wants to start using Virtual Smart Cards on its laptops and tablets, which run Windows 8 Pro.
Before implementing any changes, the client wants to ensure that the laptops and tablets support Virtual Smart Cards.
You need to verify that the client laptops and tablets support Virtual Smart Cards.
What should you do?
A. Ensure that each laptop and tablet can read a physical smart card.
B. Ensure that BitLocker Drive Encryption is enabled on a system drive of the laptops and
tablets.
C. Ensure that each laptop and tablet has a Trusted Platform Module (TPM) chip of version 1.2
or greater.
D. Ensure that the laptops and tablets are running Windows 8 Enterprise edition.
Answer: C
Explanation:
Understanding and Evaluating Virtual Smart Cards
Reference:
http://www.microsoft.com/en-au/download/confirmation.aspx?id=29076
TPM virtual smart cards Virtual smart cards (VSCs) emulate the functionality of traditional smart cards, but instead of requiring the purchase of additional hardware, they utilize technology that users already own and are more likely to have with them at all times.
Microsoft virtual smart card platform is currently limited to the use of the Trusted Platform Module (TPM) chip onboard most modern computers.
100% 70-689 Complete Success & Money Back Guarantee!
By utilizing Braindump2go high quality Microsoft 70-689 Exam Dumps Products, You can surely pass 70-689 certification 100%! Braindump2go also offers 100% money back guarantee to individuals in case they fail to pass Microsoft 70-689 in one attempt.