March/2023 Latest Braindump2go AZ-500 Exam Dumps with PDF and VCE Free Updated Today! Following are some new Braindump2go AZ-500 Real Exam Questions!
QUESTION 239
You work for an organization that has above 100 Windows Server 2016 virtual machines (VMs). Those VMs are running in the Azure West Europe region. Azure Automation runbook is used by the machines to automatically start and stop. Azure Update Management is used to manage updates. You get to know about a Microsoft security vulnerability which is affecting the Windows Server 2016 operating system (OS). When a hotfix is installed, the vulnerability gets fixed. You need to create a report of the systems that do not have the hotfix installed. What would be your step of action to generate the report?
A. Use WMI to connect remotely to each machine and search for the hotfix.
Export the results to a CSV file.
B. Use the Get-Hotfix command to connect remotely to each machine and search for the hotfix.
Export the results to a CSV file.
C. Use the Get-Childltem command to connect remotely to each machine and search for the hotfix.
Export the results to a CSV file.
D. Use Update Management from the automation account.
Select the hotfix from the missing updates list.
Export the results to a CSV file.
Answer: D
QUESTION 240
You work for an organization as an Azure administrator. There is one subscription having all Azure resources and all of them are in a single region. The organization has an Active Directory (AD) domain that is synchronized from on-premises using Azure AD Connect. Active Directory Federation Services (ADFS) is used for Single Sign-On (SSO). A managed SQL instance named Database1 is deployed to Azure with a single-user database. The users have to be authenticated when they connect, for which you use SQL Server authentication. A concern put front by the users says they are required to remember a separate username and password when if they want Excel to be connected to the managed SQL instance. As a solution, you decide to configure the Azure SQL Database so users can login without having to enter a username and password. Can you identify from the options below, which two actions should you perform?
A. Configure an Azure AD administrator for Database1
B. Deploy an on-premises data gateway in the on-premises network
C. Connect to Database1 via SQL Server Management Studio (SSMS) and enable Windows authentication.
D. Grant Database1 access to Azure AD
Answer: D
QUESTION 241
You are working for an organization as an Azure administrator. You are tasked to migrate an on-premises SQL Server to four Azure SQL databases in a single Azure SQL Server. The SQL Server audit logs were copied to an Azure Blob storage before migrating to Azure. There is a quarterly review carried with the audit logs for any suspicious activity. You are required to make sure Auditing events of all Azure SQL databases must be logged and stored for review. You should be careful with the costs as they should be minimum. Can you identify the two actions you should perform? (opt any TWO).
A. Enable auditing at the database level.
B. Configure Azure Storage as the audit log destination.
C. Enable auditing at the server level.
D. Configure Azure Event Hub as the audit log destination.
Answer: BC
QUESTION 242
There is an Azure App Service app you are managing. This app hosts website artifacts in a general purpose v2 storage account. You are required to execute the App Service app configuration so it can authenticate programmatically to the storage account. Choose which of the following would you create.
A. an Azure AD Connect VM
B. an Azure AD user
C. an Azure role-based access control (RBAC) role assignment
D. A managed identity
Answer: D
QUESTION 243
You are working for an organization managing its Azure subscription. The subscription is called Sub1 and is associated with Company1, an Azure Active Directory (Azure AD) tenant. There is another Azure AD tenant that the organization’s IT department is managing. That tenant is called corp-company1.com. A new administrator, Admin1, is hired by the organization. Admin1 has the following identities: -An account in company1.com named Identity1 -An account in corp-company1.com named Identity2 -An Outlook.com account named Identity3 You are required to transfer Sub1 ownership to Admin1. Can you identify the identities from Admin1 that might be used to transfer Sub1 ownership?
A. Identity1 only
B. Identity1 and Identity2 only
C. Identity2 only
D. Identity1, Identity2, and Identity3
Answer: B
QUESTION 244
You are working for an organization as an Azure administrator. The keys for Azure Service Bus are stored and accessed by Azure Key Vault used by several applications that organization is using. The keys are manually regenerated and stored in the key vault and this process is a little time taking. What would be your step of action if you want to configure Azure to rotate the keys automatically?
A. Set the keys to auto rotate with an expiration date of 6 months.
B. Use a scheduled task and PowerShell to expire the keys and generate new ones.
C. Grant each application permission to rotate the keys.
D. Use an Automation account and a runbook to rotate keys.
Answer: D
QUESTION 245
You work for a company managing its Azure Virtual Machine (VM). The VM is running Windows Server named and is called VM1. You are tasked to perform emergency security configuration on VM1 for which you decide to use Serial Console. What will be your first step of action?
A. Connect vm1 to an Azure Log Analytics workspace. .
B. Redeploy vm1.
C. Deploy the Desired State Configuration VM extension to vm1.
D. Enable boot diagnostics on vm1
Answer: D
QUESTION 246
You work for an organization as an Azure administrator. There was an audit exercise that surfaced the fact that numerous privileged users have accounts without multi-factor authentication (MFA) enabled. Now you need to filter out those privileged accounts on which MFA must be enabled. What would be your step of action?
A. Use Microsoft Graph API list credentialUserRegistrationDetails report and export the results to JSON.
Filter the results where isMfaRegistered is false.
B. Run an LDAP query and export the results to CSV.
Filter the results where the StrongAuthenticationRequirements.State value is empty.
C. Run the Get-MsolUser cmdlet and export the results to CSV.
Filter the results where the StrongAuthenticationRequirements.State value is empty.
D. Find the MFA alert on the recommendations tile in Security Center.
Expand the affected resources section.
Answer: D
QUESTION 247
You work for an organization that has offices in multiple regions across the world. There is a local file server at each office where departmental data is stored. Your company creates a storage account for a pilot of Azure File Sync for a remote office. 192.168.1.0/24 is the subnet used by the remote office. You need to make sure storage account can be accessed from nowhere other than the remote office. What will be your step of action?
A. Create a Network Security Group (NSG) and create two rules: one rule that blocks all Server Message Block (SMB) traffic and one rule that allows SMB traffic from 192.168.1.0/24.
Put the allow rule below the deny rule.
B. Create a custom Azure role and allow the “Microsoft.Storager/read” DataActions permission for the 192.168.1.0/24 subnet.
Assign the Azure role to the storage account.
C. Configure the storage account to allow access from selected networks.
Allow only the 192.168.1.0/24 subnet.
D. Create a Network Security Group (NSG) and create two rules: one rule that blocks all Server Message Block (SMB) traffic and one rule that allows SMB traffic from 192.168.1.0/24.
Put the allow rule above the deny rule.
Answer: C
QUESTION 248
Your organization wants to share some confidential drawings of a new design project with a customer. You are asked to provide read-only access to the files containing drawings, with the files configured to stay with the customer for a short period of time, accessible from customer’s office. A static IP address is used to connect to the internet at the customer’s office. You need to provide the most cost-effective, secure solution. Which of the following is the best step to take?
A. Create a new web application and enable the Secure File Transfer Protocol (SFTP) feature. Provide the customer with the web application URL.
B. Create a new virtual machine (VM) using the B1S Stock Keeping Unit (SKU). Create a network share on the VM, copy the drawings to the share and grant access only to the customer. Assign the VM a public IP address and share the IP and details with the customer.
C. Create a blob container. Generate a new shared access signature (SAS) allowing read access from the customer IP. Provide the customer with the URL to the container including the SAS.
D. Create a new virtual machine (VM) using the B1S Stock Keeping Unit (SKU). Create a network share on the VM, copy the drawings to the share and grant access only to the customer. Assign the VM a public IP address and share the IP and details with the customer.
Answer: C
QUESTION 249
There is a web application being developed by your company. The app requires API access to a general purpose v2 storage account in Azure. You want to regenerate the access keys from the storage account on a schedule. What would be your step of action?
A. Configure Azure Key Vault to store access keys for the storage account.
B. Enable hierarchical namespace for the storage account
C. Implement storage service encryption for the storage account.
D. Enforce secure transfer for the storage account.
Answer: A
QUESTION 250
VNet1 is an Azure virtual network (VNet) where several development servers of the company are running. There development team has numerous Docker images stored in a private repository. These container images are planned to be deployed in Azure using Azure Container Instances (ACI). You need to restrict access to these containers to VNet1. What will be your next step of action?
A. Deploy the container instances into VNet1.
B. Use a managed identity with the container instances
C. Modify the role-based access control (RBAC) permissions on the container instances.
D. Add a Domain Name System (DNS) name label to each container instance
Answer: A
QUESTION 251
You work for an organization using Azure Active Directory (Azure AD) Privileged Identity Management (PIM). You want Abby Brown, a user, to request administrative role elevation before he takes any administrative action in Azure. What should be your step of action?
A. Assign Abby Brown the Eligible role membership type.
B. Perform a resource audit on Abby Brown.
C. Invite Abby Brown to an access review.
D. Require Abby Brown to use Azure multi-factor authentication (MFA).
Answer: A
QUESTION 252
Your organization stores Docker images for internal development using Azure Container Registry. You are required to configure the registry in such a way that a registry name is needed by developers to log into the registry and an access key is required as the password. What would be your step of action?
A. Create a system-assigned managed identity.
B. Define a service endpoint for the registry.
C. Assign the developers to the AcrPull role-based access control (RBAC) role.
D. Enable the admin user in the registry.
Answer: D
QUESTION 253
There are four Azure virtual machines (VMs) in your company. Windows Server 2016 is run on all the VMs and located on a subnet named web1 in a virtual network (VNet) named vnet1. The four Azure VMs are called web1, web2. web3, and web4. Following are the requirements of inbound network traffic: -TCP 443 (all VMs) -TCP 1444 (web1, web3) Knowing this situation, can you identify the number of network security groups (NSGs) you need?
A. 3
B. 2
C. 4
D. 1
Answer: B
QUESTION 254
There are six Azure virtual machines (VMs)in your organization. The VMs are running Linux. Your organization has a line-of-business (LOB) application and these six VMs form the web tier of this LOB application. You want the key application services to start programmatically. Which of the following do you think you should use?
A. Application security group (ASG)
B. Custom script extension
C. Webjob
D. Login App
Answer: B
QUESTION 255
You work for a company running five Windows Server 2012 R2 virtual machines (VMs). The VMs are located in the Azure West Europe region. The VMs were originally deployed from the Azure marketplace. There is presently a n antivirus solution installed and is expected to become end of life soon. The company wants to now replace the old antivirus solution with Microsoft Antimalware. You are required to enable Microsoft Antimalware on each VM and do it with zero manual interaction. What would be your next step of action?
A. Add the Microsoft Antimalware extension on each VM using the Azure portal.
B. Download the Microsoft Antimalware MSI package and install it manually on each VM.
C. Use the Install-WindowsFeature command on each VM to install the Microsoft Antimalware feature.
D. Download the Microsoft Antimalware MSI package and install it on each VM by using the Desired State Configuration (DSC).
Answer: A
QUESTION 256
You are working for a company as an Azure administrator. There are above 100 virtual machines (VMs) and all running on a single tenant. That one tenant has three subscriptions. Security alerts are reported to have increased within Azure Security Center. You must make sure you receive a notification immediately as the alerts are detected in Security Center. Identify the action(s) you must perform. Each correct answer presents part of the solution
A. Create a new workspace. Connect the VMs to the workspace and gather the Windows security logs.
B. Create an Azure Automation account. Configure the account to scan for alerts in Security Center.
C. Create a new playbook. Configure the playbook to send an email whenever Security Center detects a threat.
D. Create an Azure Automation account. Configure the account to scan for alerts in Security Center.
Answer: C
QUESTION 257
There is a team of developers and data scientists and you are a security administrator on that team. It is planned to use Azure Databricks to perform data analysis. You are tasked to design an Azure-based storage repository with these requirements met: -Hadoop-compatible file system -File-level access control lists -Shared access signature (SAS) token support Identify which of the following would you create?
A. Data Lake Storage Gent
B. Data Lake Storage Gen2
C. Azure SQL Data Warehouse
D. General purpose v1 storage account
Answer: B
QUESTION 258
Your organization has a Microsoft SQL Server 2019 database. The database is hosted on an Azure virtual machine (VM). There is a web application that uses the database as its data store. The page speed of customers shopping is cart is noticeably slow. What will you do if you want tp know what stored is being called when customers access this page?
A. Choose Display Estimated Execution Plan from the Query menu.
B. Choose Include Actual Execution Plan from the Query menu.
C. Create a SQL Server Profiler trace
D. Call the SET SHOWPLAN TEXT statement in Query Analyzer.
Answer: C
QUESTION 259
Your company has an Azure SQL database. The database also consists of sensitive data. You want the prevent sensitive data from appearing as plain text inside the database system. What would be your step of action?
A. Configure Dynamic Data Masking (DDM).
B. Enable Advanced Data Security (ADS).
C. Configure Always Encrypted.
D. Enable Transparent Data Encryption (TDE).
Answer: C
QUESTION 260
A company has a single Azure subscription on resources are deployed. There is a resource group where company’s production resources are created. That resource group is called production-rg. There is another resource group where company’s development resources are created. That resource group is called development-rg. The development team is assigned the Contributor role to the development-rg resource group. The development team uses three software to make regular configuration changes to the resources of development-rg, as part of their testing. They use the Azure portal, PowerShell, and Azure CLI. You want to make sure development team can work without having the existing files deleted by any user. What would you do?
A. Remove the development team from the Contributor role and assign them the Reader role on the development-rg resource group.
B. Create a ReadOnly lock on the development-rg resource group.
C. Create a CanNotDelete lock on the development-rg resource group.
D. Create a custom role that contains the “Microsoft.Compute/virtualMachines/delete” operation in the NotActions property. Assign the role to the development-rg resource group and the development team.
Answer: C
QUESTION 261
You work for a company as an Azure administrator. There is a third party email scanning system used by the organization. The system scans email every time an email is sent to or received by Microsoft Office 365. The solution supports single sign-on (SSO) and has advanced mail scanning, reporting, and quarantine features. There is a recipient verification feature in the third-party email scanning system. A non-interactive Azure enterprise app is used to connect that feature to the tenant directory. The application verifies the sending email address before allowing the email to be sent. You are required to know what configurations are set regarding the permissions on the Azure enterprise app. Identify the two actions you must take. (opt any TWO)
A. Verify that only the correct Admin consent permissions are configured.
B. Review the Enterprise Application in Security Center.
C. Verify that the correct User and Admin consent permissions are configured.
D. Review the Enterprise Application in Azure Active Directory.
Answer: A
QUESTION 262
You have an Azure subscription that is linked to an Azure Active Directory (Azure AD) tenant.
From the Azure portal, you register an enterprise application.
Which additional resource will be created in Azure AD?
A. a service principal
B. an X.509 certificate
C. a managed identity
D. a user account
Answer: A
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-how-applications-are-added
QUESTION 263
You plan to create an Azure Kubernetes Service (AKS) cluster in an Azure subscription.
The manifest of the registered server application is shown in the following exhibit.
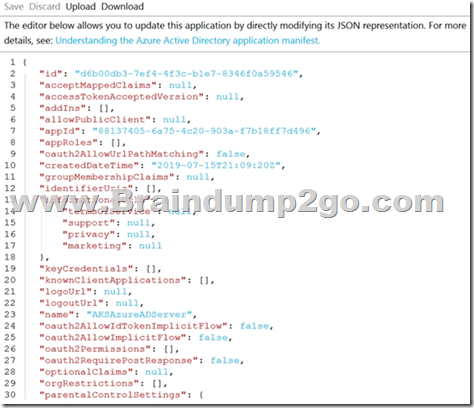
You need to ensure that the AKS cluster and Azure Active Directory (Azure AD) are integrated.
Which property should you modify in the manifest?
A. accessTokenAcceptedVersion
B. keyCredentials
C. groupMembershipClaims
D. acceptMappedClaims
Answer: C
Explanation:
https://docs.microsoft.com/en-us/azure/aks/azure-ad-integration-cli
https://www.codeproject.com/Articles/3211864/Operation-and-Maintenance-of-AKS-Applications
QUESTION 264
Hotspot Question
You plan to implement an Azure function named Function1 that will create new storage accounts for containerized application instances.
You need to grant Function1 the minimum required privileges to create the storage accounts. The solution must minimize administrative effort.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
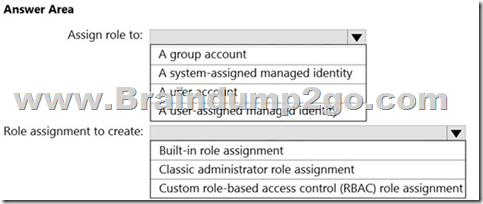
Answer:
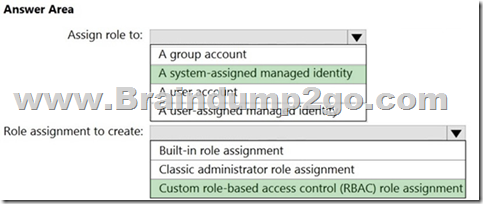
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/managed-identities-azure-resources/overview
https://docs.microsoft.com/en-us/azure/active-directory/managed-identities-azure-resources/howto-assign-access-portal
QUESTION 265
Hotspot Question
You have an Azure Active Directory (Azure AD) tenant that contains the resources shown in the following table.
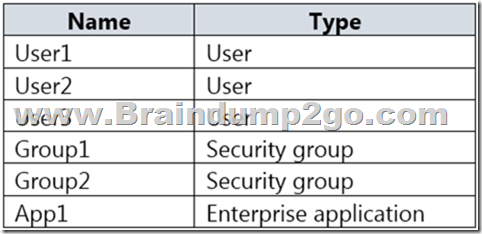
User2 is the owner of Group2.
The user and group settings for App1 are configured as shown in the following exhibit.
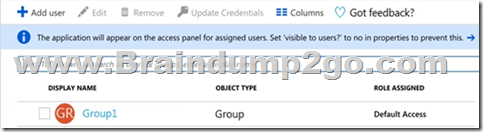
You enable self-service application access for App1 as shown in the following exhibit.
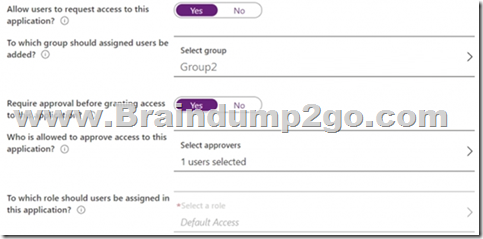
User3 is configured to approve access to Appl.
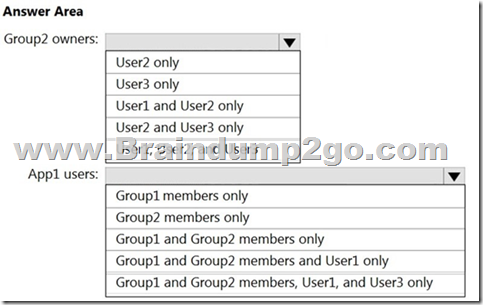
You need to identify the owners of Group2 and the users of Appl.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Answer:
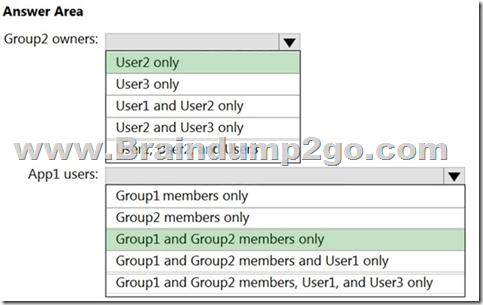
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/manage-self-service-access
QUESTION 266
Hotspot Question
You have an Azure subscription that contains a storage account named storage1 and several virtual machines. The storage account and virtual machines are in the same Azure region. The network configurations of the virtual machines are shown in the following table.
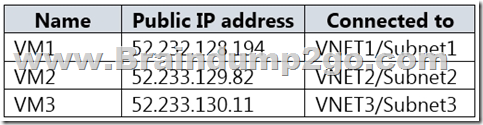
The virtual network subnets have service endpoints defined as shown in the following table.

You configure the following Firewall and virtual networks settings for storage1:
– Allow access from: Selected networks
– Virtual networks: VNET3\Subnet3
– Firewall – Address range: 52.233.129.0/24
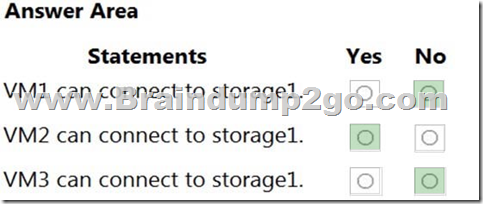
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Answer:
Explanation:
Box 1: No
VNet1 has a service endpoint configure for Azure Storage. However, the Azure storage does not allow access from VNet1 or the public IP address of VM1.
Box 2: Yes
VNet2 does not have a service endpoint configured. However, the Azure storage allows access from the public IP address of VM2.
Box 3: No
Azure storage allows access from VNet3. However, VNet3 does not have a service endpoint for Azure storage. The Azure storage also does not allow access from the public IP of VM3.
QUESTION 267
Hotspot Question
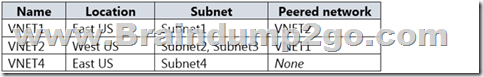
You have the Azure virtual networks shown in the following table.
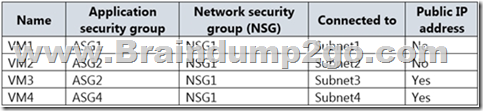
You have the Azure virtual machines shown in the following table.
The firewalls on all the virtual machines allow ping traffic.
NSG1 is configured as shown in the following exhibit.
Inbound security rules
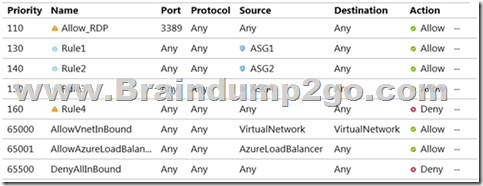
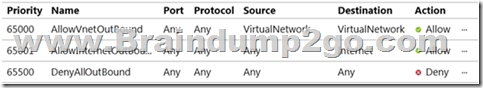
Outbound security rules
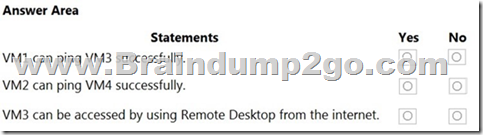
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Answer:
Explanation:
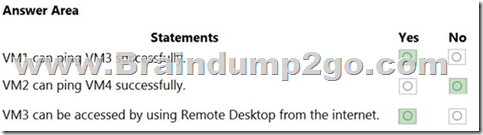
Box 1: Yes
VM1 and VM3 are on peered VNets. The firewall rules with a source of ASG1 and ASG2 allow `any’ traffic on `any’ protocol so pings are allowed between VM1 and VM3.
Box 2: No
VM2 and VM4 are on separate VNets and the VNets are not peered. Therefore, the pings would have to go over the Internet. VM4 does have a public IP and the firewall allows pings. However, for VM2 to be able to ping VM4, VM2 would also need a public IP address. In Azure, pings don’t go out through the default gateway as they would in a physical network. For an Azure VM to ping external IPs, the VM must have a public IP address assigned to it.
Box 3: Yes
VM3 has a public IP address and the firewall allows traffic on port 3389.
QUESTION 268
Hotspot Question
On Monday, you configure an email notification in Azure Security Center to email notifications to [email protected].
On Tuesday, Security Center generates the security alerts shown in the following table.
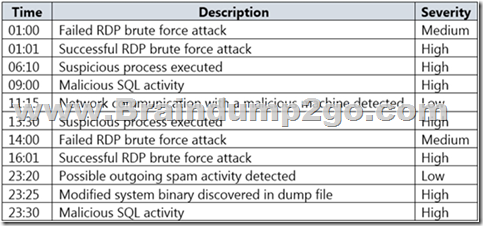
How many email notifications will [email protected] receive on Tuesday? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Answer:
Explanation:
https://docs.microsoft.com/en-us/azure/security-center/security-center-provide-security-contact-details
QUESTION 269
You are troubleshooting a security issue for an Azure Storage account.
You enable the diagnostic logs for the storage account.
What should you use to retrieve the diagnostics logs?
A. Azure Security Center
B. Azure Monitor
C. the Security admin center
D. Azure Storage Explorer
Answer: B
Explanation:
https://docs.microsoft.com/en-us/azure/storage/blobs/monitor-blob-storage?tabs=azure-portal
QUESTION 270
You have an Azure subscription that contains the resources shown in the following table.
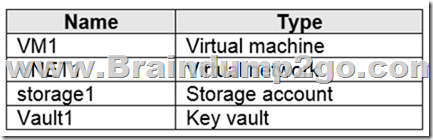
You plan to enable Azure Defender for the subscription.
Which resources can be protected by using Azure Defender?
A. VM1, VNET1, storage1, and Vault1
B. VM1, VNET1, and storage1 only
C. VM1, storage1, and Vault1 only
D. VM1 and VNET1 only
E. VM1 and storage1 only
Answer: A
Explanation:
https://docs.microsoft.com/en-us/azure/security-center/azure-defender
QUESTION 271
You have an Azure subscription that contains a resource group named RG1 and a security group named ServerAdmins. RG1 contains 10 virtual machines, a virtual network named VNET1, and a network security group (NSG) named NSG1. ServerAdmins can access the virtual machines by using RDP.
You need to ensure that NSG1 only allows RDP connections to the virtual machines for a maximum of 60 minutes when a member of ServerAdmins requests access.
What should you configure?
A. an Azure policy assigned to RG1
B. a just in time (JIT) VM access policy in Azure Security Center
C. an Azure Active Directory (Azure AD) Privileged Identity Management (PIM) role assignment
D. an Azure Bastion host on VNET1
Answer: B
Explanation:
https://docs.microsoft.com/en-us/azure/security-center/just-in-time-explained
QUESTION 272
You have a web app named WebApp1.
You create a web application firewall (WAF) policy named WAF1.
You need to protect WebApp1 by using WAF1.
What should you do first?
A. Deploy an Azure Front Door.
B. Add an extension to WebApp1.
C. Deploy Azure Firewall.
Answer: A
Explanation:
https://docs.microsoft.com/en-us/azure/frontdoor/quickstart-create-front-door
QUESTION 273
You have an Azure subscription that contains an Azure SQL database named sql1.
You plan to audit sql1.
You need to configure the audit log destination. The solution must meet the following requirements:
– Support querying events by using the Kusto query language.
– Minimize administrative effort.
What should you configure?
A. an event hub
B. a storage account
C. a Log Analytics workspace
Answer: C
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/reports-monitoring/tutorial-log-analytics-wizard
QUESTION 274
Hotspot Question
You have a management group named Group1 that contains an Azure subscription named sub1. Sub1 has a subscription ID of 11111111-1234-1234-1234-1111111111.
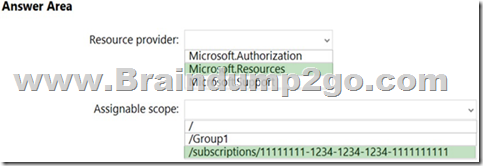
You need to create a custom Azure role-based access control (RBAC) role that will delegate permissions to manage the tags on all the objects in Group1.
What should you include in the role definition of Role1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
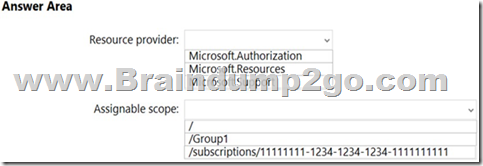
Answer:
Explanation:
Note: Assigning a custom RBAC role as the Management Group level is currently in preview only. So, for now the answer to the assignable scope is the subscription level.
Reference:
https://docs.microsoft.com/en-us/azure/role-based-access-control/resource-provider-operations
https://docs.microsoft.com/en-us/azure/role-based-access-control/custom-roles
https://docs.microsoft.com/en-us/azure/role-based-access-control/custom-roles-portal#step-5-assignable-scopes
QUESTION 275
Hotspot Question
You have an Azure subscription that contains the custom roles shown in the following table.
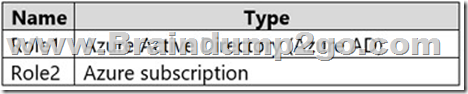
In the Azure portal, you plan to create new custom roles by cloning existing roles. The new roles will be configured as shown in the following table.
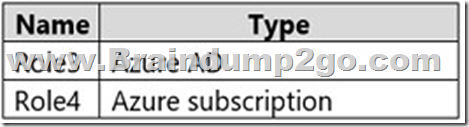
Which roles can you clone to create each new role? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
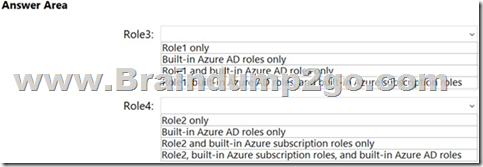
Answer:
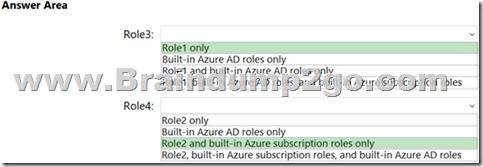
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/roles/custom-create
https://docs.microsoft.com/en-us/azure/role-based-access-control/custom-roles-portal
QUESTION 276
Drag and Drop Question
You have an Azure subscription that contains the following resources:
– A network virtual appliance (NVA) that runs non-Microsoft firewall software and routes all outbound traffic from the virtual machines to the internet
– An Azure function that contains a script to manage the firewall rules of the NVA
– Azure Security Center standard tier enabled for all virtual machines
– An Azure Sentinel workspace
– 30 virtual machines
You need to ensure that when a high-priority alert is generated in Security Center for a virtual machine, an incident is created in Azure Sentinel and then a script is initiated to configure a firewall rule for the NVA.
How should you configure Azure Sentinel to meet the requirements? To answer, drag the appropriate components to the correct requirements. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
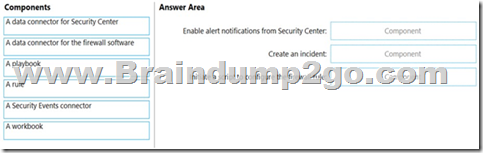
Answer:
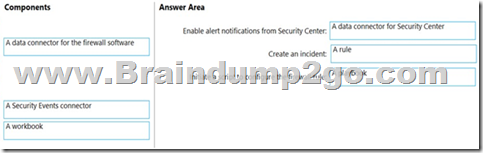
Explanation:
https://docs.microsoft.com/en-us/azure/sentinel/create-incidents-from-alerts
https://docs.microsoft.com/en-us/azure/sentinel/connect-azure-security-center
QUESTION 277
Hotspot Question
You have an Azure subscription named Subscription1 that contains the resources shown in the following table.
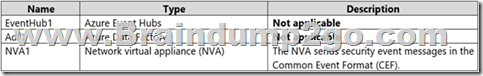
You have an Azure subscription named Subscription2 that contains the following resources:
– An Azure Sentinel workspace
– An Azure Event Grid instance
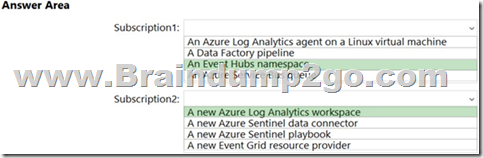
You need to ingest the CEF messages from the NVAs to Azure Sentinel.
What should you configure for each subscription? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
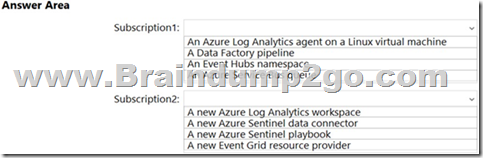
Answer:
QUESTION 278
SIMULATION
You need to ensure that the rg1lod10598168n1 Azure Storage account is encrypted by using a key stored in the KeyVault10598168 Azure key vault.
To complete this task, sign in to the Azure portal.
Answer: See the explanation below.
Explanation::
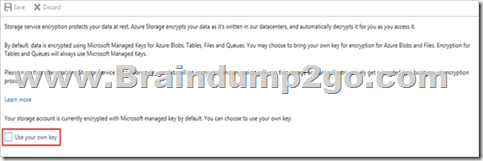
Step 1: To enable customer-managed keys in the Azure portal, follow these steps:
1. Navigate to your storage account rg1lod10598168n1
2. On the Settings blade for the storage account, click Encryption. Select the Use your own key option, as shown in the following figure.
Step 2: Specify a key from a key vault
To specify a key from a key vault, first make sure that you have a key vault that contains a key. To specify a key from a key vault, follow these steps:
4. Choose the Select from Key Vault option.
5. Choose the key vault KeyVault10598168 containing the key you want to use.
6. Choose the key from the key vault.
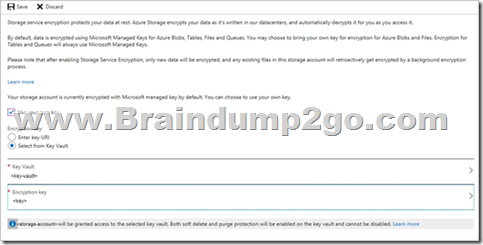
Reference:
https://docs.microsoft.com/en-us/azure/storage/common/storage-encryption-keys-portal
Resources From:
1.2023 Latest Braindump2go AZ-500 Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/az-500.html
2.2023 Latest Braindump2go AZ-500 PDF and AZ-500 VCE Dumps Free Share:
https://drive.google.com/drive/folders/1sQAsVdJ79oBKFiswxjUzGT6Gt6a6PYWl?usp=sharing
Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!