QUESTION 111
Your network contains a RADIUS server named Server1.
You install a new server named Server2 that runs Windows Server 2012 R2 and has Network Policy Server (NPS) installed.
You need to ensure that all accounting requests for Server2 are forwarded to Server1. On Server2, you create a new remote RADIUS server group named Group1 that contains Server1.
What should you configure next on Server2?
To answer, select the appropriate node in the answer area.
![clip_image001_thumb_thumb_thumb_thum[2]_thumb_thumb_thumb_thumb_thumb_thumb clip_image001_thumb_thumb_thumb_thum[2]_thumb_thumb_thumb_thumb_thumb_thumb](http://examgod.com/l2pimages/be42ce9facc7_8AD9/clip_image001_thumb_thumb_thumb_thum2_thumb_thumb_thumb_thumb_thumb_thumb_thumb.jpg)
Answer:
![clip_image0014_thumb_thumb_thumb_thu[1]_thumb_thumb_thumb_thumb_thumb_thumb clip_image0014_thumb_thumb_thumb_thu[1]_thumb_thumb_thumb_thumb_thumb_thumb](http://examgod.com/l2pimages/be42ce9facc7_8AD9/clip_image0014_thumb_thumb_thumb_thu1_thumb_thumb_thumb_thumb_thumb_thumb_thumb.jpg)
Explanation:
Connection request policies are sets of conditions and settings that allow network administrators to designate which Remote Authentication Dial-In User Service (RADIUS) servers perform the authentication and authorization of connection requests that the server running Network Policy Server (NPS) receives from RADIUS clients. Connection request policies can be configured to designate which RADIUS servers are used for RADIUS accounting. http://technet.microsoft.com/en-us/library/cc753603.aspx
QUESTION 112
Your network contains an Active Directory domain named contoso.com. The domain contains a RADIUS server named Server1 that runs Windows Server 2012 R2. You add a VPN server named Server2 to the network. On Server1, you create several network policies. You need to configure Server1 to accept authentication requests from Server2.
Which tool should you use on Server1?
A. Connection Manager Administration Kit (CMAK).
B. Routing and Remote Access
C. Network Policy Server (NPS)
D. Set-RemoteAccessRadius
Answer: C
Explanation:
Forward requests to the following remote RADIUS server group . By using this setting, NPS forwards connection requests to the remote RADIUS server group that you specify. If the NPS server receives a valid Access-Accept message that corresponds to the Access-Request message, the connection attempt is considered authenticated and authorized. In this case, the NPS server acts as a RADIUS proxy.
http://technet.microsoft.com/en-us/library/cc753603.aspx http://www.youtube.com/watch?v=0_1GOBTL4FE
QUESTION 113
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1. Server1 has the DHCP Server server role and the Network Policy Server role service installed. Server1 contains three non-overlapping scopes named Scope1, Scope2, and Scope3. Server1 currently provides the same Network Access Protection (NAP) settings to the three scopes.
You modify the settings of Scope1 as shown in the exhibit. (Click the Exhibit button.)
You need to configure Server1 to provide unique NAP enforcement settings to the NAP non- compliant DHCP clients from Scope1.
What should you create?
![clip_image0016_thumb_thumb_thumb_thu[1]_thumb_thumb_thumb_thumb_thumb_thumb clip_image0016_thumb_thumb_thumb_thu[1]_thumb_thumb_thumb_thumb_thumb_thumb](http://examgod.com/l2pimages/be42ce9facc7_8AD9/clip_image0016_thumb_thumb_thumb_thu1_thumb_thumb_thumb_thumb_thumb_thumb_thumb.jpg)
A. A network policy that has the MS-Service Class condition
B. A network policy that has the Identity Type condition
C. A connection request policy that has the Identity Type condition
D. A connection request policy that has the Service Type condition
Answer: A
Explanation:
A. Restricts the policy to clients that have received an IP address from a DHCP scope that matches the specified DHCP profile name. This condition is used only when you are deploying NAP with the DHCP enforcement method. To use the MS-Service Class attribute, in Specify the profile name that identifies your DHCP scope, type the name of an existing DHCP profile. http://technet.microsoft.com/en-us/library/cc731220(v=ws.10).aspx
QUESTION 114
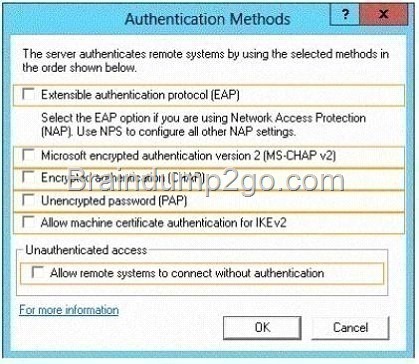
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the Remote Access server role installed.
You have a client named Client1 that is configured as an 802.1X supplicant.
You need to configure Server1 to handle authentication requests from Client1. The solution must minimize the number of authentication methods enabled on Server1.
Which authentication method should you enable?
To answer, select the appropriate authentication method in the answer area.
Answer:
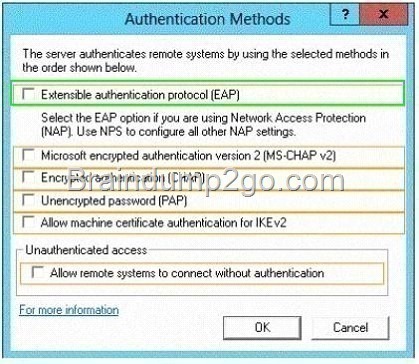
Explanation:
Microsoft Windows uses EAP to authenticate network access for Point-to-Point Protocol (PPP) connections (dial-up and virtual private network) and for IEEE 802.1X-based network access to authenticating Ethernet switches and wireless access points (APs). http://technet.microsoft.com/en-us/library/bb457039.aspx
QUESTION 115
Drag and Drop Question
Your network contains an Active Directory domain named adatum.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 is configured as a Network Policy Server (NPS) server and as a DHCP server.
You need to log all DHCP clients that have Windows Firewall disabled.
Which three actions should you perform in sequence? To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct order.
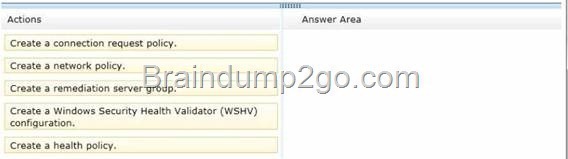
Answer:
![clip_image0026_thumb_thumb_thumb_thu[2]_thumb_thumb_thumb_thumb_thumb_thumb clip_image0026_thumb_thumb_thumb_thu[2]_thumb_thumb_thumb_thumb_thumb_thumb](http://examgod.com/l2pimages/be42ce9facc7_8AD9/clip_image0026_thumb_thumb_thumb_thu2_thumb_thumb_thumb_thumb_thumb_thumb_thumb.jpg)
Explanation:
http://technet.microsoft.com/es-es/library/dd314198%28v=ws.10%29.aspx
http://technet.microsoft.com/es-es/magazine/2009.05.goat.aspx
http://technet.microsoft.com/es-es/library/dd314173%28v=ws.10%29.aspx
http://ripusudan.wordpress.com/2013/03/19/how-to-configure-nap-enforcement-for-dhcp/ http://technet.microsoft.com/es-es/magazine/2009.05.goat.aspx
http://technet.microsoft.com/en-us/library/dd125379%28v=ws.10%29.aspx http://technet.microsoft.com/en-us/library/cc772356%28v=ws.10%29.aspx
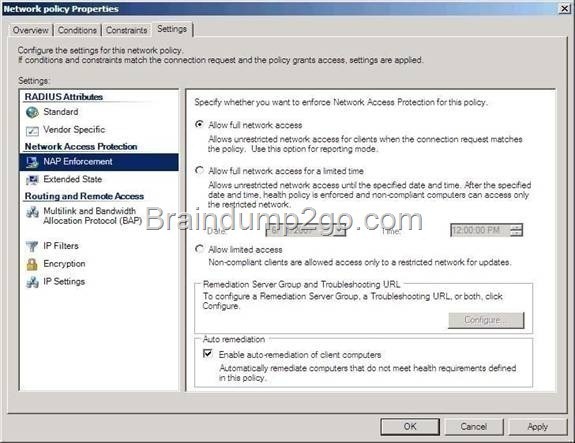
QUESTION 116
Drag and Drop Question
Your network contains an Active Directory domain named adatum.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 is configured as a Network Policy Server (NPS) server and as a DHCP server.
You need to log all DHCP clients that have Windows Firewall disabled.
Which three actions should you perform in sequence?
To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct order.
A. Create a connection request policy
B. Create Network Policy
C. Create remediation server group
D. Create Windows Security Health Validator (VSHV)
E. Create a health Policy
Answer: BDE
Explanation:
http://technet.microsoft.com/es-es/magazine/2009.05.goat.aspx
http://technet.microsoft.com/es-es/library/dd314173%28v=ws.10%29.aspx
QUESTION 117
Hotspot Question
You have a server named LON-SVR1 that runs Windows Server 2012 R2. LON-SVR1 has the Remote Access server role installed. LON-SVRl is located in the perimeter network.
The IPv4 routing table on LON-SVR1 is configured as shown in the following exhibit. (Click the Exhibit button.)
Your company purchases an additional router named Router1. Router1 has an interface that connects to the perimeter network and an interface that connects to the Internet. The IP address of the interface that connects to the perimeter network is 172.16.0.2.
You need to ensure that LON-SVR1 will route traffic to the Internet by using Router1 if the current default gateway is unavailable.
How should you configure the static route on LON-SVR1?
To answer, select the appropriate static route in the answer area.
![clip_image00212_thumb_thumb_thumb_th[2]_thumb_thumb_thumb_thumb_thumb_thumb clip_image00212_thumb_thumb_thumb_th[2]_thumb_thumb_thumb_thumb_thumb_thumb](http://examgod.com/l2pimages/be42ce9facc7_8AD9/clip_image00212_thumb_thumb_thumb_th2_thumb_thumb_thumb_thumb_thumb_thumb_thumb.jpg)
Answer:
![clip_image00214_thumb_thumb_thumb_th[1]_thumb_thumb_thumb_thumb_thumb_thumb clip_image00214_thumb_thumb_thumb_th[1]_thumb_thumb_thumb_thumb_thumb_thumb](http://examgod.com/l2pimages/be42ce9facc7_8AD9/clip_image00214_thumb_thumb_thumb_th1_thumb_thumb_thumb_thumb_thumb_thumb_thumb.jpg)
QUESTION 118
Your network contains an Active Directory domain named contoso.com. The domain contains 2 WSUS servers, ServerA and ServerB. ServerB is a replica server of ServerA. You need to configure WSUS to report data from SERVERB to SERVERA What should you configure?
A. Update Reports
B. Synchronization
C. Computer Groups
D. Reporting Rollup
Answer: D
Explanation:
Explanation:
D. You can use Reports in Windows Server Update Services (WSUS) 3.0 SP2 to monitor the WSUS network, including updates, client computers, and downstream servers. If a WSUS server has replica servers, you can roll up client status information for the replica servers to the upstream server.
http://technet.microsoft.com/en-us/library/dd939891(v=ws.10).aspx
QUESTION 119
Your network contains an Active Directory domain named adatum.com. You have a Group Policy object (GPO) that configures the Windows Update settings. Currently, client computers are configured to download updates from Microsoft Update servers. Users choose when the updates are installed. You need to configure all client computers to install Windows updates automatically.
Which setting should you configure in the GPO? To answer, select the appropriate setting in the answer area.
![clip_image00218_thumb_thumb_thumb_th[1]_thumb_thumb_thumb_thumb_thumb_thumb clip_image00218_thumb_thumb_thumb_th[1]_thumb_thumb_thumb_thumb_thumb_thumb](http://examgod.com/l2pimages/be42ce9facc7_8AD9/clip_image00218_thumb_thumb_thumb_th1_thumb_thumb_thumb_thumb_thumb_thumb_thumb.jpg)
Answer:
![clip_image00220_thumb_thumb_thumb_th[2]_thumb_thumb_thumb_thumb_thumb_thumb clip_image00220_thumb_thumb_thumb_th[2]_thumb_thumb_thumb_thumb_thumb_thumb](http://examgod.com/l2pimages/be42ce9facc7_8AD9/clip_image00220_thumb_thumb_thumb_th2_thumb_thumb_thumb_thumb_thumb_thumb_thumb.jpg)
Explanation:
http://support.microsoft.com/kb/328010#method1
QUESTION 120
Your network contains an Active Directory domain called contoso.com. The domain contains a member server named Server1. Server1 runs Windows Server 2012 R2.
You enable the EventLog-Application event trace session.
You need to set the maximum size of the log file used by the trace session to 10 MB.
From which tab should you perform the configuration?
To answer, select the appropriate tab in the answer area.
![clip_image00114_thumb_thumb_thumb_th[2]_thumb_thumb_thumb_thumb_thumb_thumb clip_image00114_thumb_thumb_thumb_th[2]_thumb_thumb_thumb_thumb_thumb_thumb](http://examgod.com/l2pimages/be42ce9facc7_8AD9/clip_image00114_thumb_thumb_thumb_th2_thumb_thumb_thumb_thumb_thumb_thumb_thumb.jpg)
Answer:
![clip_image00116_thumb_thumb_thumb_th[2]_thumb_thumb_thumb_thumb_thumb_thumb clip_image00116_thumb_thumb_thumb_th[2]_thumb_thumb_thumb_thumb_thumb_thumb](http://examgod.com/l2pimages/be42ce9facc7_8AD9/clip_image00116_thumb_thumb_thumb_th2_thumb_thumb_thumb_thumb_thumb_thumb_thumb.jpg)
Explanation:
Note: By default, logging stops only if you set an expiration date as part of the logging schedule. Using the options on the Stop Condition tab, you can configure the log file to stop automatically after a specified period of time, such as seven days, or when the log file is full (if you’ve set a maximum size limit).
http://technet.microsoft.com/en-us/magazine/ff458614.aspx
Download Free Braindump2go New Updated Microsoft 70-411 Dumps Full Version, In PDF Format, 295 Questions and Answers in all: http://www.braindump2go.com/70-411.html
![clip_image00210_thumb_thumb_thumb_th[1]_thumb_thumb_thumb_thumb_thumb_thumb clip_image00210_thumb_thumb_thumb_th[1]_thumb_thumb_thumb_thumb_thumb_thumb](http://examgod.com/l2pimages/be42ce9facc7_8AD9/clip_image00210_thumb_thumb_thumb_th1_thumb_thumb_thumb_thumb_thumb_thumb_thumb.jpg)