QUESTION 1
Your network contains two clusters. The clusters are configured as shown in the following table.
![clip_image001_thumb_thumb_thumb_thum[1] clip_image001_thumb_thumb_thumb_thum[1]](http://examgod.com/l2pimages/fc0abe88e520_C578/clip_image001_thumb_thumb_thumb_thum1_thumb.jpg)
All of the servers in both of the clusters run Windows Server 2012.
You need to plan the application of Windows updates to the nodes in the cluster.
What should you include in the plan? More than one answer choice may achieve the goal. Select the BEST answer.
A. Cluster-Aware Updating (CAU) self-updating and downloaded updates from Windows Server Update Services (WSUS)
B. Microsoft System Center 2012 Service Manager integrated with Windows Server Update Service (WSUS)
C. A manual application of Windows updates on all of the cluster node
D. Microsoft System Center 2012 Configuration Manager integrated with Windows Server Update Service (WSUS)
Answer: A
QUESTION 2
Your network contains an Active Directory domain named contoso.com. The network contains a server named Server1 that has the Hyper-V server role installed. Server1 hosts a virtual machine named VM1.
You deploy a new standalone server named Server2.
You install the Hyper-V server role on Server2. Another administrator named Admin1 plans to create a replica of VM1 on Server2.
You need to ensure that Admin1 can configure Server2 to receive a replica of VM1.
To which group should you add Admin1?
A. Server Operators
B. Domain Admins
C. Hyper-V Administrators
D. Replicator
Answer: C
QUESTION 3
Your network contains an Active Directory domain named contoso.com. The domain contains 20 servers that run Windows Server 2012. The domain contains a Microsoft System Center 2012 infrastructure. A web application named WebApp1 is installed on the 20 servers.
You plan to deploy a custom registry key for WebApp1 on the 20 servers.
You need to deploy the registry key to the 20 servers. The solution must ensure that you can verify whether the registry key was applied successfully to the servers. What should you do?
More than one answer choice may achieve the goal. Select the BEST answer.
A. From Operations Manager, create a monitor.
B. From the Group Policy Management console, create a Group Policy object (GPO).
C. From Configuration Manager, create a Compliance Settings.
D. From Orchestrator Runbook Designer, create a runbook.
Answer: C
Explanation:
![clip_image002_thumb_thumb_thumb_thum[2] clip_image002_thumb_thumb_thumb_thum[2]](http://examgod.com/l2pimages/fc0abe88e520_C578/clip_image002_thumb_thumb_thumb_thum2_thumb.jpg)
http://technet.microsoft.com/en-us/library/gg682139.aspx
QUESTION 4
Your network contains servers that run Windows Server 2012. The network contains two servers named Server1 and Server2 that are connected to a SAS storage device. The device only supports two connected computers. Server1 has the iSCSI Target Server role service installed. Ten application servers use their iSCSI Initiator to connect to virtual disks in the SAS storage device via iSCSI targets on Server1. Currently, Server2 is used only to run backup software.
You install the iSCSI Target Server role service on Server2.
You need to ensure that the iSCSI targets are available if Server1 fails.
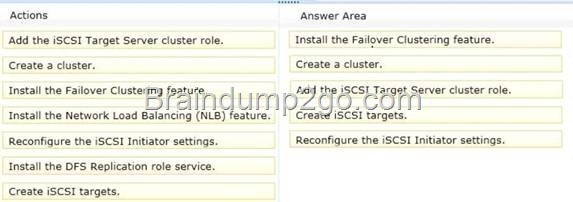
Which five actions should you perform?
To answer, move the five appropriate actions from the list of actions to the answer area and arrange them in the correct order.
![clip_image0024_thumb_thumb_thumb_thu[2] clip_image0024_thumb_thumb_thumb_thu[2]](http://examgod.com/l2pimages/fc0abe88e520_C578/clip_image0024_thumb_thumb_thumb_thu2_thumb.jpg)
Answer:
Explanation:
http://blogs.msdn.com/b/clustering/archive/2012/05/01/10299698.aspx
QUESTION 5
Your network contains multiple servers that run Windows Server 2012.
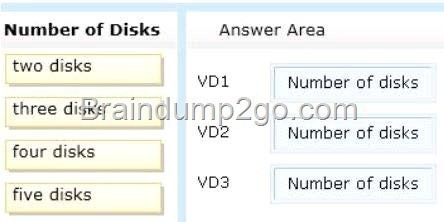
You plan to implement three virtual disks. The virtual disks will be configured as shown in the following table.
![clip_image0014_thumb_thumb_thumb_thu[1] clip_image0014_thumb_thumb_thumb_thu[1]](http://examgod.com/l2pimages/fc0abe88e520_C578/clip_image0014_thumb_thumb_thumb_thu1_thumb.jpg)
You need to identify the minimum number of physical disks required for each virtual disk.
How many disks should you identify?
To answer, drag the appropriate number of disks to the correct virtual disk in the answer area. Each number of disks may be used once, more than once, or not at all. Additionally, you may need to drag the split bar between panes or scroll to view content.
Answer:
![clip_image0018_thumb_thumb_thumb_thu[1] clip_image0018_thumb_thumb_thumb_thu[1]](http://examgod.com/l2pimages/fc0abe88e520_C578/clip_image0018_thumb_thumb_thumb_thu1_thumb.jpg)
Explanation:
http://technet.microsoft.com/es-es/library/jj822938.aspx
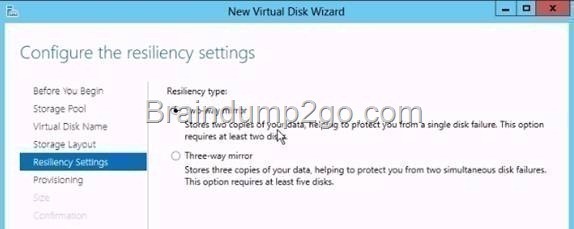
They are not talking about Clusters, a single server only, so a standalone server.
QUESTION 6
Your network contains an Active Directory domain named contoso.com. You currently have an intranet web site that is hosted by two Web servers named Web1 and Web2. Web1 and Web2 run Windows Server 2012. Users use the name intranet.contoso.com to request the web site and use DNS round robin. You plan to implement the Network Load Balancing (NLB) feature on Web1 and Web2. You need to recommend changes to the DNS records for the planned implementation. What should you recommend?
A. Create one alias (CNAME) record named Intranet. Map the CNAME record to Intranet.
B. Delete both host (A) records named Intranet. Create a pointer (PTR) record for each Web server.
C. Create a new host (A) record named Intranet. Remove both host (A) records for Web1 and Web2.
D. Delete one of the host (A) records named Intranet. Modify the remaining host (A) record named Intranet.
Answer: C
QUESTION 7
Your network contains five servers that run Windows Server 2012.
You install the Hyper-V server role on the servers.
You create an external virtual network switch on each server.
You plan to deploy five virtual machines to each Hyper-V server. Each virtual machine will have a virtual network adapter that is connected to the external virtual network switch and that has a VLAN identifier of 1. Each virtual machine will run Windows Server 2012. All of the virtual machines will run the identical web application.
You plan to install the Network Load Balancing (NLB) feature on each virtual machine and join each virtual machine to an NLB cluster. The cluster will be configured to use unicast only.
You need to ensure that the NLB feature can distribute connections across all of the virtual machines. What should you do?
A. From the properties of each virtual machine, add a second virtual network adapter.
Connect the new virtual network adapters to the external virtual network switch.
Configure the new virtual network adapters to use a VLAN identifier of 2.
B. On each Hyper-V server, create a new private virtual network switch.
From the properties of each virtual machine, add a second virtual network adapter.
Connect the new virtual network adapters to the new private virtual network switches.
C. On each Hyper-V server, create a new external virtual network switch.
From the properties of each virtual machine, add a second virtual network adapter.
Connect the new virtual network adapters to the new external virtual network switches.
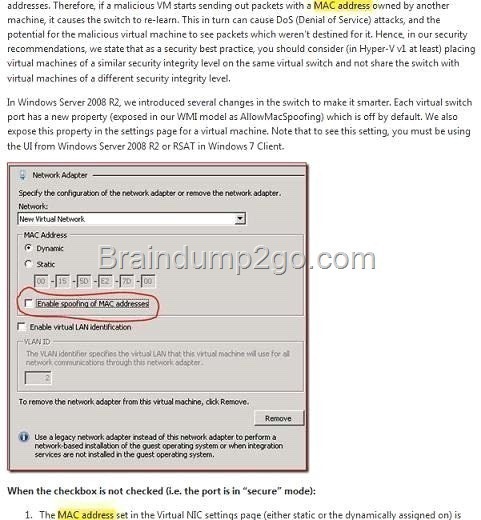
D. From the properties of each virtual machine, enable MAC address spoofing for the existing virtual network adapter.
Answer: D
Explanation:
MAC spoofing
The changing of the assigned MAC address may allow the bypassing of access control lists on servers or routers, either hiding a computer on a network or allowing it to impersonate another network device. A user may wish to legitimately spoof the MAC address of a previous hardware device in order to reacquire connectivity after hardware failure.
http://blogs.technet.com/b/jhoward/archive/2009/05/21/new-in-hyper-v-windows-server-2008-r2- part-2-macspoofing.aspx
QUESTION 8
Your network contains a server named Server1 that runs Windows Server 2012. Server1 is configured as a Hyper-V host. Server1 hosts a virtual machine named VM1. VM1 is configured as a file server that runs Windows Server 2012. VM1 connects to a shared storage device by using the iSCSI Initiator.
You need to back up the files and the folders in the shared storage used by VM1.
The solution must ensure that open files are included in the backup. What should you do?
A. From Hyper-V Manager, create a snapshot of VM1.
B. From Server1, perform a backup by using Windows Server Backup.
C. From VM1, perform a backup by using Windows Server Backup.
D. From Microsoft System Center 2012 Virtual Machine Manager (VMM), create a copy of VM1.
Answer: C
Explanation:
Backing Up Hyper-V Virtual Machines Using Windows Server Backup
http://blogs.msdn.com/b/taylorb/archive/2008/08/20/backing-up-hyper-v-virtual-machines-using- windowsserver-backup.aspx
QUESTION 9
Your network contains three networks named LAN1, LAN2, and LAN3.
You have a Hyper-V host named Hyper1 that has Windows Server 2012 installed. Hyper1 has three network adapters. The network adapters are configured as shown in the following table.
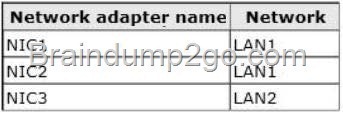
Hyper1 hosts 10 virtual machines. A virtual machine named VM1 runs a line-of-business application that is used by all of the users of LAN1. All of the other virtual machines are connected to LAN2.
You need to implement a solution to ensure that users can access VM1 if either NIC1 or NIC2 fails. What should you do?
A. From the properties of each virtual network adapter, enable network adapter teaming, and then modify the bandwidth management settings.
B. From the properties of each virtual network adapter, enable network adapter teaming, and then enable virtual LAN identification.
C. From the properties of each physical network adapter, enable network adapter teaming, and then add a second legacy network adapter to VM1.
D. From the properties of each physical network adapter, enable network adapter teaming, and then create a virtual switch.
Answer: D
QUESTION 10
Your network contains an Active Directory domain named contoso.com.
You deploy Microsoft System Center 2012 Virtual Machine Manager (VMM). The network contains five physical servers. The servers are configured as shown in the following table.
![clip_image00114_thumb_thumb_thumb_th[2] clip_image00114_thumb_thumb_thumb_th[2]](http://examgod.com/l2pimages/fc0abe88e520_C578/clip_image00114_thumb_thumb_thumb_th2_thumb.jpg)
You plan to use VMM to convert the existing physical servers to virtual machines.
You need to identify which physical servers can be converted to virtual machines.
Which servers should you identify? (Each correct answer presents part of the solution. Choose all that apply.)
A. Server1
B. Server2
C. Server3
D. Server4
E. Server5
Answer: ADE
Explanation:
http://technet.microsoft.com/en-us/systemcenter/hh278293.aspx
Download Braindump2go’s Latest Microsoft 70-414 Dump Full Version For Free: http://www.braindump2go.com/70-414.html