QUESTION 145
Hotspot Question
Your network contains an Active Directory forest named northwindtraders.com.
The client computers in the finance department run either Windows 8.1, Windows 8, or Windows 7. All of the client computers in the marketing department run Windows 8.1.
You need to design a Network Access Protection (NAP) solution for northwindtraders.com that meets the following requirements:
– The client computers in the finance department that run Windows 7 must have a firewall enabled and the antivirus software must be up-to-date.
– The finance computers that run Windows 8.1 or Windows 8 must have automatic updating enabled and the antivirus software must be up-to-date.
– The client computers in the marketing department must have automatic updating enabled and the antivirus software must be up-to-date.
– If a computer fails to meet its requirements, the computers must be provided access to a limited set of resources on the network.
– If a computer meets its requirements, the computer must have full access to the network.
What is the minimum number of objects that you should create to meet the requirements? To answer, select the appropriate number for each object type in the answer area.
![clip_image0024_thumb_thumb_thumb_thu[1]_thumb_thumb_thumb_thumb_thumb clip_image0024_thumb_thumb_thumb_thu[1]_thumb_thumb_thumb_thumb_thumb](http://examgod.com/l2pimages/4c82c1c32824_C674/clip_image0024_thumb_thumb_thumb_thu1_thumb_thumb_thumb_thumb_thumb_thumb.jpg)
QUESTION 146
You have a System Center 2012 R2 Virtual Machine Manager (VMM) infrastructure that manages five Hyper-V hosts. The Hyper-V hosts are not clustered.
You have a virtual machine template that deploys a base image of Windows Server 2012 R2. No role services or features are enabled in the base image.
You need to deploy a virtual machine named VM1 that is based on the virtual machine template.
VM1 will be deployed as part of a service. VM1 must have the Web Server (IIS) server role installed. The solution must not require modifications to the virtual machine template or the base image.
What are two possible profile types that achieve the goal? Each correct answer presents a complete solution.
A. Capability
B. Application
C. Guest OS
D. Hardware
E. Physical Computer
Answer: BC
QUESTION 147
Your company plans to hire 100 sales representatives who will work remotely.
Each sales representative will be given a laptop that will run Windows 7. A corporate image of Windows 7 will be applied to each laptop.
While the laptops are connected to the corporate network, they will be joined to the domain. The sales representatives will not be local administrators.
Once the laptops are configured, each laptop will be shipped by courier to a sales representative.
The sales representative will use a VPN connection to connect to the corporate network.
You need to recommend a solution to deploy the VPN settings for the sales representatives. The solution must meet the following requirements:
Ensure that the VPN settings are the same for every sales representative. Ensure that when a user connects to the VPN, an application named App1 starts.
What is the best approach to achieve the goal? More than one answer choice may achieve the goal. Select the BEST answer.
A. VPN auto triggering
B. The Add-VpnConnectioncmdlet
C. The Connection Manager Administration Kit (CMAK)
D. Group Policy preferences
Answer: C
QUESTION 148
Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains four servers. The servers are configured as shown in the following table.
![clip_image0018_thumb_thumb_thumb_thu[2]_thumb_thumb_thumb_thumb_thumb clip_image0018_thumb_thumb_thumb_thu[2]_thumb_thumb_thumb_thumb_thumb](http://examgod.com/l2pimages/4c82c1c32824_C674/clip_image0018_thumb_thumb_thumb_thu2_thumb_thumb_thumb_thumb_thumb_thumb.jpg)
You plan to provide users with the ability to use Workplace Join for their personal device when they connect to the internal network.
You need to recommend a certificate configuration for the planned deployment.
What should you include in the recommendation? To answer, select the appropriate names in the answer area.
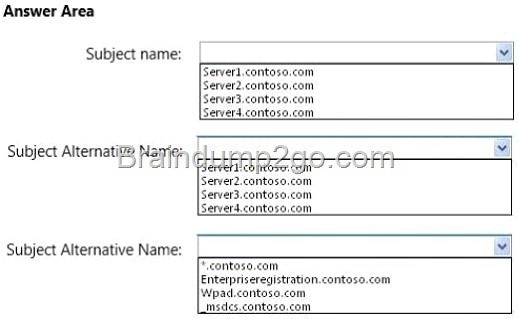
Answer:
![clip_image00110_thumb_thumb_thumb_th[1]_thumb_thumb_thumb_thumb_thumb clip_image00110_thumb_thumb_thumb_th[1]_thumb_thumb_thumb_thumb_thumb](http://examgod.com/l2pimages/4c82c1c32824_C674/clip_image00110_thumb_thumb_thumb_th1_thumb_thumb_thumb_thumb_thumb_thumb.jpg)
QUESTION 149
Drag and Drop Question
Your network contains an Active Directory forest named adatum.com. The forest contains a single domain. All servers run Windows Server 2012 R2. All client computers run Windows 8.1.
The DNS zone of adatum.com is Active Directory-integrated.
You need to implement DNSSEC to meet the following requirements:
– Ensure that the zone is signed.
– Ensure that the zone signing key (ZSK) changes every 30 days.
– Ensure that the key signing key (KSK) changes every 365 days.
What should you do? To answer, drag the appropriate cmdlets to the correct requirements. Each cmdlet may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
![clip_image0026_thumb_thumb_thumb_thu[2]_thumb_thumb_thumb_thumb_thumb clip_image0026_thumb_thumb_thumb_thu[2]_thumb_thumb_thumb_thumb_thumb](http://examgod.com/l2pimages/4c82c1c32824_C674/clip_image0026_thumb_thumb_thumb_thu2_thumb_thumb_thumb_thumb_thumb_thumb.jpg)
Answer:
![clip_image0028_thumb_thumb_thumb_thu[1]_thumb_thumb_thumb_thumb_thumb clip_image0028_thumb_thumb_thumb_thu[1]_thumb_thumb_thumb_thumb_thumb](http://examgod.com/l2pimages/4c82c1c32824_C674/clip_image0028_thumb_thumb_thumb_thu1_thumb_thumb_thumb_thumb_thumb_thumb.jpg)
QUESTION 150
Your company has two main offices and 10 branch offices. Each office is configured as a separate Active Directory site.
The main offices sites are named Site1 and Site2. Each office connects to Site1 and Site2 by using a WAN link. Each site contains a domain controller that runs Windows Server 2008.
You are redesigning the Active Directory infrastructure.
You plan to implement domain controllers that run Windows Server 2012 and decommission all of the domain controllers that run Windows Server 2008.
You need to recommend a placement plan for the Windows Server 2012 domain controllers to meet the following requirements:
– Ensure that users can log on to the domain if a domain controller or a WAN link fails.
– Minimize the number of domain controllers implemented.
What should you include in the recommendation? (Each correct answer presents part of the solution. Choose all that apply.)
A. Read-only domain controllers (RODCs) in the branch office sites
B. A writable domain controller in Site1
C. A writable domain controller in Site2
D. Writable domain controllers in the branch office sites
Answer: ABC
QUESTION 151
Hotspot Question
You run the ldifde command and receive the following output:
![clip_image00210_thumb_thumb_thumb_th[2]_thumb_thumb_thumb_thumb_thumb clip_image00210_thumb_thumb_thumb_th[2]_thumb_thumb_thumb_thumb_thumb](http://examgod.com/l2pimages/4c82c1c32824_C674/clip_image00210_thumb_thumb_thumb_th2_thumb_thumb_thumb_thumb_thumb_thumb.jpg)
The command completes successfully.
Use the drop-down menus to select the answer choice that completes each statement.
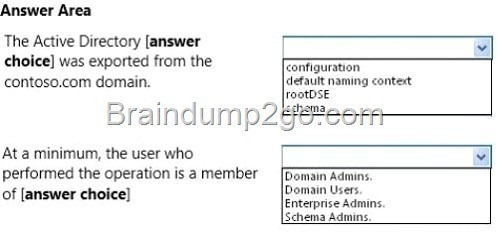
Answer:
![clip_image00212_thumb_thumb_thumb_th[1]_thumb_thumb_thumb_thumb_thumb clip_image00212_thumb_thumb_thumb_th[1]_thumb_thumb_thumb_thumb_thumb](http://examgod.com/l2pimages/4c82c1c32824_C674/clip_image00212_thumb_thumb_thumb_th1_thumb_thumb_thumb_thumb_thumb_thumb.jpg)
QUESTION 152
Your network contains an Active Directory domain named contoso.com. Your company has an enterprise root certification authority (CA) named CA1. You plan to deploy Active Directory Federation Services (AD FS) to a server named Serverl. The company purchases a Microsoft Office 365 subscription. You plan register the company’s SMTP domain for Office 365 and to configure single sign-on for all users. You need to identify which certificate or certificates are required for the planned deployment. Which certificate or certificates should you identify? (Each correct answer presents a complete solution. Choose all that apply.)
A. a server authentication certificate that is issued by a trusted third-party root CA and that contains the subject name serverl.contoso.com
B. a server authentication certificate that is issued by CA1 and that contains the subject name Server1
C. a server authentication certificate that is issued by a trusted third-party root CA and that contains the subject name Server1
D. a server authentication certificate that is issued by CA1 and that contains the subject name serverl.contoso.com
E. self-signed server authentication certificates for serverl.contoso.com
Answer: DE
Explanation:
Use the full name. The subject name is commonly represented by using an X.500 or Lightweight Directory Access Protocol (LDAP) format.
QUESTION 153
Your network contains a server named Server1 that runs Windows Server 2012. Server1 is configured as a Hyper-V host. Server1 hosts a virtual machine named VM1. VM1 is configured as a file server that runs Windows Server 2012. VM1 connects to a shared storage device by using the iSCSI Initiator. You need to back up the files and the folders in the shared storage used by VM1. The solution must ensure that open files are included in the backup. What should you do?
A. From Hyper-V Manager, create a snapshot of VM1.
B. From Server1, perform a backup by using Windows Server Backup.
C. From VM1, perform a backup by using Windows Server Backup.
D. From Microsoft System Center 2012 Virtual Machine Manager (VMM), create a copy of VM1.
Answer: C
Explanation:
Backing Up Hyper-V Virtual Machines Using Windows Server Backup
![clip_image00114_thumb_thumb_thumb_th[1]_thumb_thumb_thumb_thumb_thumb clip_image00114_thumb_thumb_thumb_th[1]_thumb_thumb_thumb_thumb_thumb](http://examgod.com/l2pimages/4c82c1c32824_C674/clip_image00114_thumb_thumb_thumb_th1_thumb_thumb_thumb_thumb_thumb_thumb.jpg)
http://blogs.msdn.com/b/taylorb/archive/2008/08/20/backing-up-hyper-v-virtual-machines-using- windowsserver-backup.aspx
QUESTION 154
Your network contains an Active Directory domain named contoso.com. You deploy Active Directory Certificate Services (AD CS). Your company, which is named Contoso, Ltd., has a partner company named Fabrikam, Inc. Fabrikam also deploys AD CS. Contoso and Fabrikam plan to exchange signed and encrypted email messages. You need to ensure that the client computers in both Contoso and Fabrikam trust each other’s email certificates. The solution must prevent other certificates from being trusted. What should you do? More than one answer choice may achieve the goal. Select the BEST answer.
A. Implement an online responder in each company.
B. Exchange the root certification authority (CA) certificates of both companies, and then deploy the certificates to the Trusted Root Certification Authorities store by using Group Policy objects (GPOs).
C. Exchange the root certification authority (CA) certificates of both companies, and then deploy the certificates to the Enterprise Trust store by using Group Policy objects (GPOs).
D. Implement cross-certification in each company.
Answer: D
Passing Microsoft 70-413 Exam successfully in a short time! Just using Braindump2go’s Latest Microsoft 70-413 Dump
http://www.braindump2go.com/70-413.html
![clip_image001_thumb_thumb_thumb_thum[2]_thumb_thumb_thumb_thumb_thumb clip_image001_thumb_thumb_thumb_thum[2]_thumb_thumb_thumb_thumb_thumb](http://examgod.com/l2pimages/4c82c1c32824_C674/clip_image001_thumb_thumb_thumb_thum2_thumb_thumb_thumb_thumb_thumb_thumb.jpg)