May/2020 New Braindump2go 300-735 Exam Dumps with PDF and VCE Free Updated Today! Following are some new 300-735 Exam Questions!
QUESTION 26
Which API is designed to give technology partners the ability to send security events from their platform/service/appliance within a mutual customer’s environment to the Umbrella cloud for enforcement?
A. Cisco Umbrella Management API
B. Cisco Umbrella Security Events API
C. Cisco Umbrella Enforcement API
D. Cisco Umbrella Reporting API
Correct Answer: C
QUESTION 27
Which two event types can the eStreamer server transmit to the requesting client from a managed device and a management center? (Choose two.)
A. user activity events
B. intrusion events
C. file events
D. intrusion event extra data
E. malware events
Correct Answer: BD
QUESTION 28
A security network engineer must implement intrusion policies using the Cisco Firepower Management Center API. Which action does the engineer take to achieve the goal?
A. Make a PATCH request to the URI /api/fmc_config/v1/domain/{DOMAIN_UUID}/policy/intrusionpolicies.
B. Make a POST request to the URI /api/fmc_config/v1/domain/{DOMAIN_UUID}/policy/intrusionpolicies.
C. Intrusion policies can be read but not configured using the Cisco Firepower Management Center API.
D. Make a PUT request to the URI /api/fmc_config/v1/domain/{DOMAIN_UUID}/policy/intrusionpolicies.
Correct Answer: C
QUESTION 29
Which curl command lists all tags (host groups) that are associated with a tenant using the Cisco Stealthwatch Enterprise API?
A. curl -X PUT”Cookie:{Cookie Data}”https://{stealthwatch_host}/smc-configuration/rest/v1/tenants/{tenant_id}/tags
B. curl -X POST -H”Cookie:{Cookie Data}”https://{stealthwatch_host}/smc-configuration/rest/v1/tenants/tags
C. curl -X GET -H”Cookie:{Cookie Data}”https://{stealthwatch_host}/smc-configuration/rest/v1/tenants/{tenant_id}/tags
D. curl -X GET -H”Cookie:{Cookie Data}”https://{stealthwatch_host}/smc-configuration/rest/v1/tenants/tags
Correct Answer: C
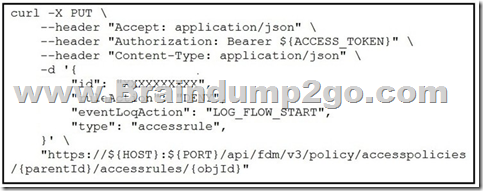
QUESTION 30
Refer to the exhibit. The security administrator must temporarily disallow traffic that goes to a production web server using the Cisco FDM REST API. The administrator sends an API query as shown in the exhibit.
What is the outcome of that action?
A. The given code does not execute because the mandatory parameters, source, destination, and services are missing.
B. The given code does not execute because it uses the HTTP method “PUT”. It should use the HTTP method “POST”.
C. The appropriate rule is updated with the source, destination, services, and other fields set to “Any” and the action set to “DENY”. Traffic to the production web server is disallowed, as expected.
D. A new rule is created with the source, destination, services, and other fields set to “Any” and the action set to “DENY”. Traffic to the production web server is disallowed, as expected.
Correct Answer: C
QUESTION 31
FILL BLANK
Fill in the blank to complete the statement with the correct technology.
Cisco Investigate provides access to data that pertains to DNS security events and correlations collected by the Cisco security team.
Correct Answer: Umbrella
QUESTION 32
Refer to the exhibit. The script outputs too many results when it is queried against the Cisco Umbrella Reporting API. Which two configurations restrict the returned result to only 10 entries? (Choose two.)
A. Add params parameter in the get and assign in the {“return”: “10”} value.
B. Add ?limit=10 to the end of the URL string.
C. Add params parameter in the get and assign in the {“limit”: “10”} value.
D. Add ?find=10 to the end of the URL string.
E. Add ?return=10 to the end of the URL string.
Correct Answer: BC
QUESTION 33
DRAG DROP
A Python script is being developed to return the top 10 identities in an organization that have made a DNS request to “www.cisco.com”. Drag and drop the code to complete the Cisco Umbrella Reporting API query to return the top identities. Not all options are used.
Select and Place:
Correct Answer:
QUESTION 34
Which two destinations are supported by the Cisco Security Management Appliance reporting APIs? (Choose two.)
A. email
B. Microsoft Word file
C. FTP
D. web
E. csv file
Correct Answer: AD
QUESTION 35
What are two capabilities of Cisco Firepower Management Center eStreamer? (Choose two.)
A. eStreamer is used to get sources for intelligence services.
B. eStreamer is used to send malware event data.
C. eStreamer is used to get a list of access control policies.
D. eStreamer is used to send policy data.
E. eStreamer is used to send intrusion event data.
Correct Answer: BE
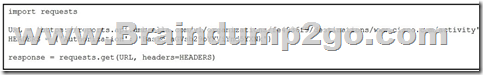
QUESTION 36
Refer to the exhibit. A security engineer created a script and successfully executed it to retrieve all currently open alerts. Which print command shows the first returned alert?
A. print(response[data][0])
B. print(response[results][0])
C. print(response.json()[data][0])
D. print(response.json()[results][0])
Correct Answer: A
QUESTION 37
Refer to the exhibit. A network operator must create a Python script that makes an API request to Cisco Umbrella to do a pattern search and return all matched URLs with category information.
Which code completes the script?
A. URL = BASE_URL + “/find/exa\[a-z\]ple.com” PARAMS = { “categoryinclude” : “true”}
B. URL = BASE_URL + “/find/exa\[a-z\]ple.com” PARAMS = { “returncategory” : “true”}
C. URL = BASE_URL + “/find/exa\[a-z\]ple.com” PARAMS = { “includeCategory” : “true”}
D. URL = BASE_URL + “/find/exa\[a-z\]ple.com” PARAMS = { “returnCategory” : “true”}
Correct Answer: D
QUESTION 38
Which two statements describe the characteristics of API styles for REST and RPC? (Choose two.)
A. REST-based APIs function in a similar way to procedures.
B. REST-based APIs are used primarily for CRUD operations.
C. REST and RPC API styles are the same.
D. RPC-based APIs function in a similar way to procedures.
E. RPC-based APIs are used primarily for CRUD operations.
Correct Answer: BD
QUESTION 39
What are two benefits of Ansible when managing security platforms? (Choose two.)
A. End users can be identified and tracked across a network.
B. Network performance issues can be identified and automatically remediated.
C. Policies can be updated on multiple devices concurrently, which reduces outage windows.
D. Anomalous network traffic can be detected and correlated.
E. The time that is needed to deploy a change is reduced, compared to manually applying the change.
Correct Answer: CE
Resources From:
1.2020 Latest Braindump2go 300-735 Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/300-735.html
2.2020 Latest Braindump2go 300-735 PDF and 300-735 VCE Dumps Free Share:
https://drive.google.com/drive/folders/1m19PdiWiEdzrVfv_C_JxguM15u1-V5mx?usp=sharing
3.2020 Free Braindump2go 300-735 PDF Download:
https://www.braindump2go.com/free-online-pdf/300-735-PDF(1-11).pdf
https://www.braindump2go.com/free-online-pdf/300-735-PDF-Dumps(34-45).pdf
https://www.braindump2go.com/free-online-pdf/300-735-VCE(23-33).pdf
https://www.braindump2go.com/free-online-pdf/300-735-VCE-Dumps((12-22).pdf
Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!