2017/July New NSE4 Exam Dumps with PDF and VCE Free Updated in www.Braindump2go.com Today!
100% NSE4 Real Exam Questions! 100% NSE4 Exam Pass Guaranteed!
1.|2017 New NSE4 Exam Dumps (PDF & VCE) 360Q&As Download:
https://www.braindump2go.com/nse4.html
2.|2017 New NSE4 Exam Questions & Answers Download:
https://drive.google.com/drive/folders/0B75b5xYLjSSNVi1ISU1vQUxBOTg?usp=sharing
QUESTION 41
Which statement is an advantage of using a hub and spoke IPsec VPN configuration instead of a fully-meshed set of IPsec tunnels?
A. Using a hub and spoke topology provides full redundancy.
B. Using a hub and spoke topology requires fewer tunnels.
C. Using a hub and spoke topology uses stronger encryption protocols.
D. Using a hub and spoke topology requires more routes.
Answer: B
QUESTION 42
Review the IKE debug output for IPsec shown in the exhibit below.

Which statements is correct regarding this output?
A. The output is a phase 1 negotiation.
B. The output is a phase 2 negotiation.
C. The output captures the dead peer detection messages.
D. The output captures the dead gateway detection packets.
Answer: C
QUESTION 43
Review the configuration for FortiClient IPsec shown in the exhibit.
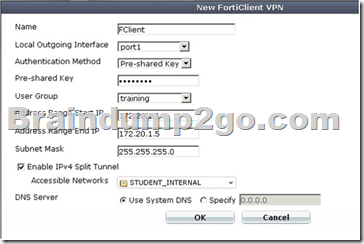
Which statement is correct regarding this configuration?
A. The connecting VPN client will install a route to a destination corresponding to the student_internal address object.
B. The connecting VPN client will install a default route.
C. The connecting VPN client will install a route to the 172.20.1.[1-5] address range.
D. The connecting VPN client will connect in web portal mode and no route will be installed.
Answer: A
QUESTION 44
Review the IPsec phase 1 configuration in the exhibit; then answer the question below.
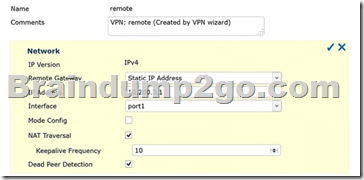
Which statements are correct regarding this configuration? (Choose two.)
A. The remote gateway address on 10.200.3.1.
B. The local IPsec interface address is 10.200.3.1.
C. The local gateway IP is the address assigned to port1.
D. The local gateway IP address is 10.200.3.1.
Answer: AC
QUESTION 45
Review the IPsec diagnostics output of the command diagnose vpn tunnel list shown in the exhibit below.

Which statements are correct regarding this output? (Choose two.)
A. The connecting client has been allocated address 172.20.1.1.
B. In the Phase 1 settings, dead peer detection is enabled.
C. The tunnel is idle.
D. The connecting client has been allocated address 10.200.3.1.
Answer: AB
QUESTION 46
Which IPsec mode includes the peer id information in the first packet?
A. Main mode.
B. Quick mode.
C. Aggressive mode.
D. IKEv2 mode.
Answer: C
QUESTION 47
Which statements are correct properties of a partial mesh VPN deployment. (Choose two.)
A. VPN tunnels interconnect between every single location.
B. VPN tunnels are not configured between every single location.
C. Some locations are reached via a hub location.
D. There are no hub locations in a partial mesh.
Answer: BC
QUESTION 48
Examine the following log message for IPS and identify the valid responses below. (Select all that apply.)
2012-07-01 09:54:28 oid=2 log_id=18433 type=ips subtype=anomaly pri=alert vd=root severity=”critical” src=”192.168.3.168″ dst=”192.168.3.170″ src_int=”port2″ serial=0 status=”detected” proto=1 service=”icmp” count=1 attack_name=”icmp_flood” icmp_id=”0xa8a4″ icmp_type=”0x08″ icmp_code=”0x00″ attack_id=16777316 sensor=”1″ ref=”http://www.fortinet.com/ids/VID16777316″ msg=”anomaly: icmp_flood, 51 > threshold 50″
A. The target is 192.168.3.168.
B. The target is 192.168.3.170.
C. The attack was detected and blocked.
D. The attack was detected only.
E. The attack was TCP based.
Answer: BD
QUESTION 49
Identify the statement which correctly describes the output of the following command:
diagnose ips anomaly list
A. Lists the configured DoS policy.
B. List the real-time counters for the configured DoS policy.
C. Lists the errors captured when compiling the DoS policy.
D. Lists the IPS signature matches.
Answer: B
QUESTION 50
Review the IPS sensor filter configuration shown in the exhibit

Based on the information in the exhibit, which statements are correct regarding the filter? (Choose two.)
A. It does not log attacks targeting Linux servers.
B. It matches all traffic to Linux servers.
C. Its action will block traffic matching these signatures.
D. It only takes effect when the sensor is applied to a policy.
Answer: CD
!!!RECOMMEND!!!
1.|2017 New NSE4 Exam Dumps (PDF & VCE) 360Q&As Download:
https://www.braindump2go.com/nse4.html
2.|2017 New NSE4 Study Gudie Video:
https://youtu.be/lcPSEfJYR0M