MICROSOFT NEWS: 70-659 Exam Questions has been Updated Today! Get Latest 70-659 VCE and 70-659 PDF Instantly! Welcome to Download the Newest Braindump2go 70-659 VCE&70-659 PDF Dumps: http://www.braindump2go.com/70-659.html (161 Q&As)
We never believe in second chances and Braindump2go brings you the best 70-659 Exam Preparation Materials which will make you pass in the first attempt.We guarantee all questions and answers in our 70-659 Dumps are the latest released,we check all exam dumps questions from time to time according to Microsoft Official Center, in order to guarantee you can read the latest questions!
Exam Code: 70-659
Exam Name: TS: Windows Server 2008 R2, Server Virtualization
Certification Provider: Microsoft
70-659 Dumps,70-659 Book,70-659 Study Guide PDF,70-659 eBook,70-659 Braindump,70-659 eBook,70-659 Exam Questions,70-659 Exam Prep,70-659 Dumps PDF,70-659 Dumps Free,70-659 Latest Dumps,70-659 Practice Exam,70-659 Practice Questions,70-659 PDF,70-659 VCE
QUESTION 101
Your company has a Microsoft Hyper-V Server 2008 R2 environment.
You manage the environment by using Microsoft System Center Virtual Machine Manager (VMM) 2008 R2
You attempt to migrate child partitions through a firewall by using network migration.
The migration fails.
You need to ensure that you can successfully complete the migration.
Which firewall port should you open?
A. 80
B. 135
C. 445
D. 8554
Answer: A
Explanation:
80 and 135 445 are the possible answers
Port to open when adding host in multisite into VMM Server
TCP/8100
TCP/80-
TCP/443-SSL
TCP/5900
TCP/3389-RDP
TCP/2179
TCP/135
TCP/445
Make sure the firewall port is open bi-directional between VMM and Hyper V Host which behind the firewall.
The host should join to domain
QUESTION 102
You are configuring a virtual machine (VM) that is running on a Windows Server 2008 R2 host server.
The primary virtual disk is connected to IDE Controller 0.
You need to add a virtual disk to the VM without shutting down the VM.
What should you do?
A. Add the virtual disk to IDE Controller 0.
B. Add the virtual disk to IDE Controller 1.
C. Add the virtual disk to an existing SCSI controller.
D. Add a virtual network adapter to the VM.
Attach an iSCSI disk to the VM through the virtual network adapter.
Answer: C
Explanation:
A similar scenario can occur when a virtual machine is running out of disk space and you want to add another virtual hard disk without shutting down the virtual machine. You can attach a virtual hard disk to a virtual machine without shutting down that virtual machine only if you attach it to the SCSI controller of the virtual machine.
To attach a virtual hard disk to an IDE controller, you must first shut down the virtual machine. Scenario prerequisites
To test this scenario, you will need the following:
Complete all steps in the main section of this guide. After you complete all the steps, you will have a virtualization server and two virtual machines:Base Virtual Machine(used for creating new virtual machines) and Imported Virtual Machine.
Imported Virtual Machine is running, Windows Server2008R2 is configured, and the computer name for the virtual machine is VirtualMachine1.
Scenario steps
The following procedure explains how to create and attach a virtual hard disk to the virtualization server, copy files to the virtual hard disk, and then attach the disk to a virtual machine without shutting it down.
To create and connect a virtual hard disk without shutting down the virtual machine On the virtualization server, create and attach a new virtual hard disk as follows:
Open Server Manager. ClickStart, point toAdministrative Tools, and then clickServer Manager.
In Server Manager, in the console tree, underStorage, clickDisk Management. After the disks on the virtualization server are listed in Disk Management, in the console tree, right-clickDisk Management, and then clickCreate VHD. TheCreate and Attach Virtual Hard Disk dialog box appears.
Type or browse to the location on the virtualization server where you want to create the virtual hard disk, and type a name for it.
Type a size for the virtual hard disk. SelectMBfor megabytes,GBfor gigabytes, orTBfor terabytes.
Select the format of the virtual hard disk: dynamically expanding or fixed size.
To create the virtual hard disk and attach it to the virtualization server, clickOK. After a few moments, the new virtual hard disk is listed in Disk Management with the other disks that are available on the virtualization server, and its state is listed asNot Initialized.
To initialize the virtual hard disk, right-click the virtual hard disk, and then clickInitialize Disk. TheInitialize Disk dialog box appears.
On theInitialize Diskdialog box, clickOK.
After a few moments, the new virtual hard disk is initialized and listed asOnline.
To create a simple volume on the virtual hard disk, right-click the virtual hard disk, and then clickNew Simple Volume. TheNew Simple Volume Wizardopens.
Follow the steps in theNew Simple Volume Wizardto create the simple volume, assign it a drive letter, and perform a quick format. After a few moments, the volume in the virtual hard disk is listed asHealthy, and a drive letter is assigned to it. The virtual hard disk is now available on the virtualization server, and can be accessed to read and write information. Optionally, copy files to the virtual hard disk so that they can be made available to the virtual machine.
Detach the virtual hard disk from the virtualization server, as follows:
In Disk Management, right-click the virtual hard disk, and then clickDetach VHD.
TheDetach Virtual Hard Disk dialog box appears.
To detach the virtual hard disk, ensure that theDelete the virtual hard disk file after removing the diskcheck box is not selected, and then clickOK. After a few moments, the virtual hard disk is no longer listed in Disk Management.
Attach the virtual hard disk to the SCSI controller of theImported Virtual Machinevirtual machine, as follows:
On the virtualization server, open Hyper-V Manager. ClickStart, point toAdministrative Tools, and then click Hyper-V Manager.
In Hyper-V Manager, underVirtual Machines, right-clickImported Virtual Machine, and then clickSettings.
TheSettings for Imported Virtual Machinedialog box appears.
In the left navigation pane, clickSCSI Controller.
InSCSI Controller, clickHard Drive, and then clickAdd. A hard drive is added to the SCSI controller and is automatically selected in the left navigation pane.
In theHard Driveproperties, clickVirtual hard disk (.vhd) file, and then clickBrowse. Browse to the location on the virtualization server where you created the virtual hard disk, and then clickOpen.
To attach the virtual hard disk to the virtual machine, clickOK. The virtual hard disk is now available on the virtual machine, and can be accessed to read and write information. Optionally, you can detach a virtual hard disk from the virtual machine and attach it again to the virtualization server, without turning off the virtual machine, as follows:
In Hyper-V Manager, underVirtual Machines, right-clickImported Virtual Machine, and then clickSettings. TheSettings for Imported Virtual Machinedialog box appears.
In the left navigation pane, underSCSI Controller, click the virtual hard disk that you want to detach from the virtual machine.
In theHard Driveproperties, clickRemove.
To detach the virtual hard disk from the virtual machine, clickOK.
The virtual disk is no longer attached to the virtual machine and can now be attached to the virtualization server. On the virtualization server, open Server Manager. ClickStart, point toAdministrative Tools, and then click Server Manager.
In Server Manager, in the console tree, underStorage, clickDisk Management. After the disks on the virtualization server are listed in Disk Management, in the console tree, right-clickDisk Management, and then clickAttach VHD. TheAttach Virtual Hard Diskdialog box appears.
Type or browse to the location on the virtualization server where you created the virtual hard disk, and then clickOK. After a few moments, the virtual hard disk is listed in Disk Management with the other disks that are available on the virtualization server, and its state is listed asOnline. The virtual hard disk is now available on the virtualization server, and can be accessed to read and write information.
QUESTION 103
You create a virtual machine (VM) on a Windows Server 2008 R2 Hyper-V server.
The VM has a single VHD file that is connected to an IDE controller.
You need to add five new virtual disks to the VM.
You must minimize the amount of virtual hardware.
What should you do?
A. Add the virtual disks to IDE Controller 0.
B. Add the virtual disks to an existing SCSI controller.
C. Remove the virtual DVD drive, and add the virtual disks to IDE Controller1.
D. Add five SCSI controllers to the VM, and add one virtual disk to each SCSI controller.
Answer: B
Explanation:
Use of virtual SCSI devices requires integration services to be installed in the guest operating system.
SCSI devices. Each virtual machine supports up to 256 SCSI disks (four SCSI controllers with each controller supporting up to 64 disks).
SCSI controllers use a type of device developed specifically for use with virtual machines and use the virtual machine bus to communicate.
The virtual machine bus must be available when the guest operating system is started. Therefore, virtual hard disks attached to SCSI controllers cannot be used as startup disks. By default, SCSI commands are filtered in Hyper-V in Windows Server 2008 R2. Although it is possible to disable filtering of SCSI commands, we do not recommend that you arbitrarily disable filtering because it represents a possible security risk (when filtering of SCSI commands is turned off, SCSI commands pass directly from the virtual machine to the storage stack on the management operating system).
Programmatically disabling SCSI filtering is supported in Hyper-V in Windows Server 2008 R2 and may be required for certain storage management applications. You should only disable SCSI filtering after consulting with your storage vendor and determining that it is necessary for application compatibility.
Although the I/O performance of physical SCSI and IDE devices can differ significantly, this is not true for the virtualized SCSI and IDE devices in Hyper-V. Hyper-V. IDE and SCSI devices both offer equally fast I/O performance when integration services are installed in the guest operating system
QUESTION 104
You are preparing to install an operating system on virtual machines (VMs) in a Hyper-V environment.
You need to configure each VM so that you can perform a network-based operating system installation.
What should you do for each VM?
A. Add a Network Adapter.
B. Add a Legacy Network Adapter.
C. Configure a static MAC address.
D. Configure a dynamic MAC address.
Answer: B
Explanation:
On the Installation Options page, choose the method you want to use to install the operating system:
Install an operating system from a boot CD/DVD-ROM.
You can use either physical media or an image file (.iso file).
Install an operating system from a boot floppy disk.
Install an operating system from a network-based installation server. To use this option, you must configure the virtual machine with a legacy network adapter connected to an external virtual network.
The external virtual network must have access to the same network as the image server.
http://technet.microsoft.com/en-us/library/cc732470(v=ws.10).aspx
QUESTION 105
Your company has an Active Directory Domain Services (AD DS) domain that includes an AD security group named Monitoring.
You are configuring a Windows Server 2008 R2 Hyper-V server that hosts several virtual machines (VMs).
You need to ensure that members of the Monitoring group can only stop and start VMs on the host server.
What should you do?
A. Add the Monitoring group to the Server Operators AD security group.
B. In Authorization Manager, add the Monitoring group to the Administrator role in the default
scope.
C. In Authorization Manager, create a task that includes the Stop Virtual Machine and Start
Virtual Machine operations.
Add the task to the Administrator role.
D. In Authorization Manager, create a role in the default scope.
Add the Stop Virtual Machine and Start Virtual Machine operations to the role.
Assign the Monitoring group to the role.
Answer: D
Explanation:
Adding administrator role to Montoring group will gain access to create a VM.
Server Operators is a local group that allows a user to perform general administrator tasks. These tasks include sharing server resources, performing file backup and recovery, and more. As with other operator accounts, Server Operators can also log on to a server locally and shut it down. Server Operators can perform most common server administration tasks. On domain controllers, members of this group can log on interactively, create and delete shared resources, start and stop some services, back up and restore files, format the hard disk, and shut down the computer. This group has no default members. Because this group has significant power on domain controllers, add users with caution.
Back up files and directories; Change the system time; Force shutdown from a remote system; Allow log on locally; Restore files and directories; Shut down the system.
http://technet.microsoft.com/en-us/library/cc756898(v=ws.10).aspx
QUESTION 106
You manage Hyper-V host servers and virtual machines (VMs) by using Microsoft System Center Virtual Machine Manager (VMM) 2008 R2.
Developers are members of an AD security group named Development.
You need to ensure that on a specific host server, members of the Development group can perform only the Create, Modify, and Remove VM management tasks.
What should you do?
A. Create a Self-Service user role and add the Development group to this role.
B. Create a Delegated Administrator user role and add the Development group to this role.
C. In Authorization Manager, create a role on the client computer of each member of the Development group, and add the Development group to this role.
D. Install Hyper-V Manager on the client computer of each member of the Development group,
and grant the Development group administrative privileges on the specific server.
Answer: A
Explanation:
The self-service user role grants users permissions to create, operate, manage, store, create checkpoints for, and connect to their own virtual machines through the Virtual Machine Manager Self-Service Portal.
In role-based security, dynamic collections of instances of objects (such as hosts or virtual machines), known as groups, determine the available targets for a particular operation that a user performs. For example, when a user attempts to start a virtual machine, VMM first checks whether the user has permission to perform the Start action on virtual machines and then verifies that the user has the right to start the selected virtual machine.
These groups are hierarchical: providing access to a particular instance provides access to all instances contained in that instance. For example, providing access to a host group provides access to all hosts within the host group and to all virtual networks on the hosts. The following illustration shows the hierarchy of instances within the groups that apply to VMM user roles.
When a user role provides access to an instance in the outer ring, it automatically provides access to all instances in the inner rings. Virtual machines are pictured separately because the flow of access works somewhat differently for them. For all administrator roles, host group rights flow to all virtual machines that are deployed on the hosts. However, that is not true for members of self-service user roles. The rights of self service users are limited to virtual machines that they own.

Group hierarchies for role-based security
Role Types in VMM
The following user role types, based on profiles of the same name, are defined for VMM:
Administrator role–Members of the Administrator role can perform all VMM actions on all objects that are managed by the VMM server. Only one role can be associated with this profile. At least one administrator should be a member of the role. Delegated Administrator role–Members of a role based on the Delegated Administrator profile have full VMM administrator rights, with a few exceptions, on all objects in the scope defined by the host groups and library that are assigned to the role. A delegated administrator cannot modify VMM settings or add or remove members of the Administrator role.
Self-Service User role–Members of a role based on the Self-Service User profile can manage their own virtual machines within a restricted environment. Self-service users use the VMM Self-Service Web Portal to manage their virtual machines. The portal provides a simplified view of only the virtual machines that the user owns and the operations that the user is allowed to perform on them. A self-service user role specifies the operations that members can perform on their own virtual machines (these can include creating virtual machines) and the templates and ISO image files that they can use to create virtual machines. The user role also can place a quota on the virtual machines that a user can deploy at any one time. Self-service users’ virtual achines are deployed transparently on the most suitable host in the host group that is assigned to the user role.
QUESTION 107
Your virtual environment includes Hyper-V host servers and VMware ESX Server hosts.
You manage the environment by using Microsoft System Center Virtual Machine Manager (VMM) 2008 R2.
You need to enable non-administrative users to manage snapshots or checkpoints for virtual machines (VMs) that are hosted on either host system.
What should you do?
A. Create checkpoints in VMM.
B. Create snapshots by using Hyper-V Manager.
C. Create checkpoints by using the VMM Self-Service Portal.
D. Create snapshots from within the Virtual Machine Connection console.
Answer: C
Explanation:
You can grant self-service users permission to create and manage checkpoints for their virtual machines.
By creating checkpoints for a virtual machine, you can restore the virtual machine to a previous state. A typical use of checkpoints is to create a temporary backup before you apply update the operating system. The checkpoint enables you to revert the virtual machine to its previous state if the update fails or adversely affects the virtual machine.
What Is a Checkpoint?
Each checkpoint saves the state of each virtual hard disk that is attached to a virtual machine and all of the hard disk’s contents, including application data files.
Use the Recover action to restore a virtual machine to its state when a checkpoint was created. For more information, seeHow to Restore a Virtual Machine to a Checkpoint. When you no longer need to recover a virtual machine to a checkpoint, you should merge the checkpoint to delete the associated files and recover disk space.
You can create as many as 64 checkpoints for any one virtual machine. However, checkpoints use disk space and, when allowed to proliferate over long periods, can affect performance during operations such as migrating a virtual machine. For this reason, it is a good practice to routinely merge unneeded checkpoints.
Checkpoints are portable. When you migrate, store, or deploy a virtual machine, any existing checkpoints move with the virtual machine.
You can create checkpoints only when a virtual machine is deployed on a host. You cannot create checkpoints when a virtual machine is stored in the library.
It is advisable to shut down the virtual machine before creating a checkpoint. However, you can create a checkpoint while a virtual machine is in a Stopped or Turned Off state. Doing so stops the virtual machine momentarily while the checkpoint is created. If Virtual Machine Additions is not installed on the virtual machine, the virtual machine is not shut down. Instead, it is simply stopped; this is similar to switching off the power on a physical machine while it is still running. To avoid losing any data, ensure that the virtual machine is not in use and that no processes are running on the virtual machine.
Several entry points are provided for creating checkpoints. You can use the New checkpoint action for a selected virtual machine, or you can create and manage checkpoints while updating the properties of a virtual machine VMM uses the same Single Port Listener technology to provide the administrator with live thumbnails in the VMM Administrator Console. The VMM Self-Service Portal and VirtualMachineViewer.exe also use the Single Port Listener technology of RDP.
Do not use checkpoints for disaster recovery. Checkpoints do not create full duplicates of the hard disk contents nor do they copy data to a separate volume. A checkpoint can serve as temporary backup before updating an operating system on a virtual machine so that you can roll back if the update has any adverse effects. You should use a backup application to back up and recover your data in case of catastrophic data loss.
Checkpoints provide a temporary backup when you need to restore a virtual machine to a previous state after a change such as a system or application update. However, you should not use checkpoints for the permanent backup of the operating system, applications, or files.
Checkpoints are stored with the virtual machine on the host. Therefore, if the host fails while the virtual machine is deployed, the checkpoints are lost. To provide data protection for your virtual machines, you should instead use the Volume Shadow Copy Service (VSS) writer for Virtual Server or a backup application such as System Center Data Protection Manager (DPM) to back up your virtual machines to external storage
QUESTION 108
You add a Windows Server 2008 R2 server with the Hyper-V role installed to an existing Hyper-V failover cluster.
After you move a virtual machine (VM) to the new cluster node, Microsoft System Center Virtual Machine Manager (VMM) 2008 R2 reports the status of the VM as Unsupported Cluster Configuration.
You need to be able to manage the VM by using VMM.
What should you do?
A. Disable TCP Chimney Offload on the new cluster nodes network adapters
B. Disable the TCP/IP Offload Engine (TOE) on the new cluster nodes network adapters.
C. Move the VM configuration file to a local storage device, and update the pointer to the file.
D. Update the virtual networking configuration of the new cluster node to match the virtual
networking configuration of the original cluster nodes.
Answer: D
Explanation:
One or more virtual network adapters on the virtual machine are not connected to a highly available virtual network.
If the virtual networks on all hosts in the host cluster do not have the same name and the same case (virtual network names are case-sensitive), a highly available virtual machine might lose connectivity when it is migrated or fails over to another cluster node. To find out the common virtual networks for the cluster, in the VMM Administrator Console, view the Networks tab in the host cluster properties. To configure virtual networks on the hosts, use the Networking tab in host properties.
For a VN to be marked as HA, The location and tag of the VN in all nodes must be the same. For each VN in the cluster:
The NICs to which the VN is attached in each node have the same location
The Tag in the VN in each node is the same
The VN Name is the same
After you commit changes, refresh the cluster so ensure that the VN is detected as HA. To check that the VNs are properly detected as HA:
In the admin console, select the cluster, right click and select properties
Go to the Virtual Networks and check that the VNs are displayed.
If a VN is not displayed, it means that location, tag or name is not consistent across the cluster nodes Lastly, if the VM has a DVD image attached, ensure that the .iso file resides in the shared storage and not in a local volume of the Host.
Go to the VM properties and in the hardware tab select the DVD driver.
Check the path to the .iso file points to a share resource.
On Windows Server 2008 R2 the difference between Balanced and High Performance is minimal:
Balanced Settings (default):
– Hard disk –> Turn off hard disk after –> 0 minutes
– Sleep –> Allow wake timers –> Enable
– USB settings –> USB selective suspend setting –> Enabled
– Power buttons and lid –> Power button action –> Shut down
– PCI Express –> Link State Power Management –> –> Moderate power savings
– Processor power management – System cooling policy –> Active
– Display –> Turn off display after –> 10 Minutes High Performance:
– Hard disk –> Turn off hard disk after –> 0 minutes
– Sleep –> Allow wake timers –> Enable
– USB settings –> USB selective suspend setting –> Enabled
– Power buttons and lid –> Power button action –> Shut down
– PCI Express –> Link State Power Management –> –> Off
– Processor power management – System cooling policy –> Active
– Display –> Turn off display after –> 15 Minutes Note: Differences indicated in bold.
If Hyper-V switch driver installation has gone corrupt.
You could either:
1. Remove/re-add the Hyper-V role
2. Uninstall and re-install the switch driver (instructions below)
For 2:
1. Close Hyper-V manager
2. close ncpa.cpl
3. “net stop nvspwmi” (from an elevated prompt)
4. “netcfg.exe -u VMS_PP” (from an elevated prompt)
5. “netcfg.exe -c p -i VMS_PP” (from an elevated prompt)
6. Reboot
In case Switch driver installation issue is still suspected then check the setupapi logs.
1. Change
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Setup\LogLevel to 0x2000ffff
2. Reboot
3. Try it again
4. check \windows\inf\setupapi.app.log and \windows\inf\setupapi.dev.log
QUESTION 109
All servers on your companys network run Windows Server 2008 R2.
You deploy Remote Desktop Services (RDS).
The company has a load-balanced Remote Desktop Connection Broker (RD Connection Broker) cluster.
You are adding a Remote Desktop Session Host (RD Session Host) server to the cluster.
You need to ensure that the RD Session Host server will receive only half of the RDS sessions.
What should you do?
A. Enable IP redirection on the RD Session Host server.
B. Enable token redirection on the RD Session Host server.
C. Configure the server weight for the RD Session Host server.
D. Configure the DNS weight priority for the RD Session Host server.
Answer: C
Explanation:
TS Session Broker Load Balancing sets a limit of 16 for the maximum number of pending logon requests to a particular terminal server. This helps to prevent the scenario where a single server is overwhelmed by new logon requests; for example, if you add a new server to the farm, or if you enable user logons on a server where they were previously denied.
The TS Session Broker Load Balancing feature also enables you to assign a relative weight value to each server. By assigning a relative weight value, you can help to distribute the load between more powerful and less powerful servers in the farm.
Additionally, a new “server draining” mechanism is provided that enables you to prevent new users from logging on to a terminal server that is scheduled to be taken down for maintenance. This mechanism provides for the ability to take a server offline without disrupting the user experience. If new logons are denied on a terminal server in the farm, TS Session Broker will allow users with existing sessions to reconnect, but will redirect new users to terminal servers that are configured to allow new logons
QUESTION 110
Your network includes the servers shown in the following table.
Per-Device Remote Desktop Services client access licenses (RDS CALs) are installed on Server1.
After you refresh a group of client computers with Windows 7, users on those computers can no longer connect to Server2.
You need to ensure that the users can connect to remote applications.
What should you do?
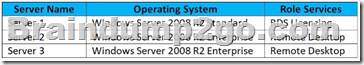
A. From the affected client computers, initiate a Remote Desktop connection to Server1.
B. From the affected client computers, initiate a Remote Desktop connection to Server3.
C. On the affected client computers, open port 3389 on the Windows Firewall.
D. On Server1, revoke the RDS device CALs of the affected client computers.
Answer: D
Explanation:
We have enabled RDS CALs per device then the computers can connect to server3 but not to server2 and vice versa. Because, RDS CALs are enabled.
Revoke the device CALs of the affected group.
Port has already been open-Not a firewall issue.
We need to fix the issue on server2 not on server1 or server3.
Braindump2go Guarantee:
Pass-Certification 70-659 offers absolute risk free investment opportunity, values your timr and money! Braindump2go latest 70-659 Real Exam Dumps – Your success in 70-659 Exam is certain! Your belief in our 70-659 Exam Dumps is further strengthened with 100% Money Back Promise from Braindump2go!
FREE DOWNLOAD: NEW UPDATED 70-659 PDF Dumps & 70-659 VCE Dumps from Braindump2go: http://www.braindump2go.com/70-659.html (161 Q&As)